Share this article

CJIS Security Policy compliance: An extensive guide
Accelerating security solutions for small businesses Tagore offers strategic services to small businesses. | A partnership that can scale Tagore prioritized finding a managed compliance partner with an established product, dedicated support team, and rapid release rate. | Standing out from competitors Tagore's partnership with Vanta enhances its strategic focus and deepens client value, creating differentiation in a competitive market. |
The Criminal Justice Information Services Division (CJIS) within the FBI manages Criminal Justice Information (CJI). Considering the highly sensitive nature of law enforcement data, you have to implement federal security standards to safeguard CJI against increasingly complex cybersecurity threats.
The CJIS Security Policy was introduced in 1992 as a framework to protect CJI through both strategic and tactical measures. It’s frequently updated to evolve with new technologies and business models. The latest version (Version 6.0) was released in December 2024.
This guide walks through the essentials of the policy, including:
- Its scope and applicability
- The 20 CJIS compliance requirements
- Compliance challenges with best practices
What is the CJIS Security Policy?
The CJIS Security Policy is a set of standards and minimum security requirements developed by the FBI’s CJIS division. Its main objective is to protect CJI across its lifecycle, from creation, modification, and storage to transmission and destruction.
CJI is all data collected, stored, and used by law enforcement agencies as part of their duties. It includes documentation relating to criminal cases, as well as audio and visual data, such as photographs, recorded interviews, and surveillance footage. The CJIS groups CJI into five categories:
- Biometrics: Unique physical traits that help identify an individual, such as fingerprints, iris scans, and facial recognition data
- Identity history: Textual information that matches biometric data and provides a history of civil and criminal events for an individual
- Biographic data: Information about individuals related to a unique case (doesn’t have to be connected to identity data)
- Property data: Property and vehicle data associated with a crime
- Case/incident history: Information about previous criminal incidents
{{cta_withimage22="/cta-blocks"}}
Why is the CJIS Security Policy important?
The CJIS Security Policy establishes the standard for securing CJI throughout its journey, from initial collection to disposal. That said, the framework only defines baseline security standards, meaning organizations can implement stricter measures to meet their security and operational needs.
The policy also enables cooperation between federal, state, and local law enforcement agencies across jurisdictions and departments. It ensures that CJI—such as criminal records and investigative information—is shared securely, without compromising its confidentiality and integrity.
Who needs to comply with the CJIS Security Policy?
Any individual or entity that processes or stores criminal or noncriminal CJI must comply with the CJIS Security Policy—this includes private organizations, contractors, noncriminal justice agency representatives, and members of a criminal justice entity. CJIS compliance is also mandatory for organizations that enter a contract with a government agency to assist with law enforcement duties.
In-scope organizations handling CJI must be authorized via an originating agency identifier (ORI), which is a unique seven-digit number assigned to each entity for access to CJIS systems.
The FBI’s CJIS Division is the primary enforcer of the policy and has the power to conduct audits on all in-scope organizations. Non-compliance can result in the loss of access to CJI, financial penalties, or legal escalation, depending on the type and severity of the violation.
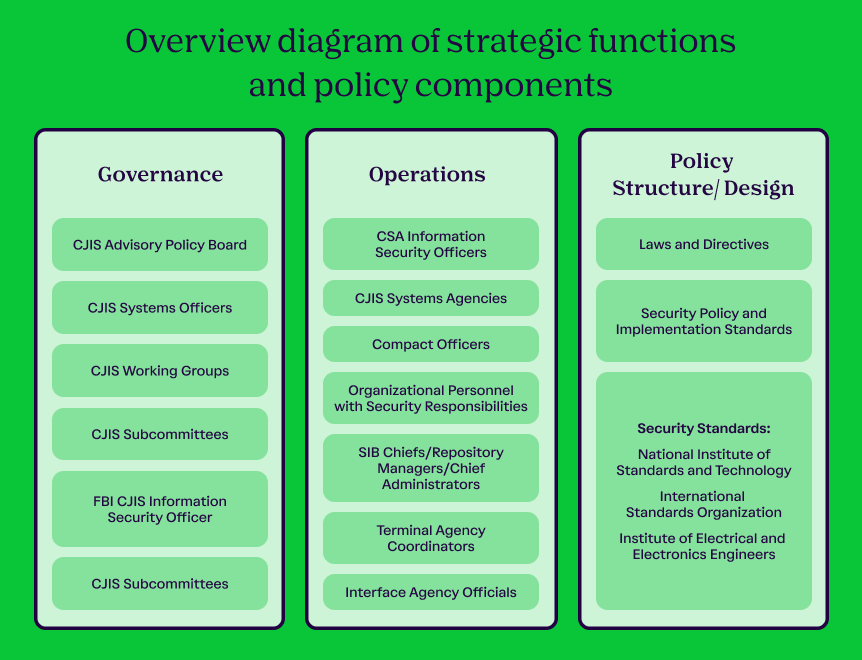
CJIS Security Policy compliance requirements
The CJIS Security Policy Version 6.0 groups compliance requirements into 20 policy areas (or control areas), each covering a different aspect of data security. The requirements are mapped to NIST 800-53 controls, which form the foundation of the policy. Organizations already aligned with NIST 800-53 or related frameworks, such as NIST 800-171, FedRAMP, or GovRAMP, can achieve CJIS Security Policy compliance faster.
The 20 policy areas of CJIS Security Policy are:
- Information Exchange Agreements
- Access Control (AC)
- Awareness and Training (AT)
- Auditing and Accountability (AU)
- Assessment, Authorization, and Monitoring (CA)
- Configuration Management (CM)
- Contingency Planning (CP)
- Identification and Authentication (IA)
- Incident Response (IR)
- Maintenance (MA)
- Media Protection (MP)
- Physical and Environmental Protection (PE)
- Planning (PL)
- Personnel Security (PS)
- Risk Assessment (RA)
- System and Services Acquisition (SA)
- Systems and Communications Protection (SC)
- System and Information Integrity (SI)
- Supply Chain Risk Management (SR)
- Mobile Devices
In the following sections, we’ll give you a brief overview of each policy area and share some tips on how to meet them.
1. Information Exchange Agreements
This policy area covers agreements that organizations must sign before sharing CJI. These agreements may outline the roles, responsibilities, and data ownership between agencies and external parties. Signing agencies are responsible for protecting CJI, so they maintain visibility into their vendors’ security postures to ensure their safeguards also meet CJIS criteria.
Common types of agreements include:
- Management control agreement: Used where a noncriminal justice agency performs services for a criminal justice organization
- Memorandum of understanding: Outlines the terms and responsibilities for sharing CJI
- Interagency connection agreement: Provides the terms and conditions for two or more criminal justice agencies to connect and share CJI
2. Access Control
This policy area requires strict access controls to minimize exposure risks to CJI. The best practice is to enforce role-based access control (RBAC) coupled with the principle of least privilege, ensuring stakeholders only access information necessary for their role.
Additionally, organizations need to assign dedicated account managers responsible for creating and disabling user accounts. Each account must be disabled within a week after it:
- Has expired
- Is no longer associated with a user
- Has violated organizational policies
- Hasn’t been used for 90 calendar days
If a user account poses a threat to CJI, the account manager must disable it within 30 minutes of the risk being flagged.
{{cta_withimage22="/cta-blocks"}}
3. Awareness and Training
To meet CJIS requirements, organizations must conduct regular personnel training sessions so stakeholders understand the risks to CJI and know how to handle it securely. These sessions should cover aspects such as recognizing insider threats, maintaining strong passwords, and incident reporting practices.
Teams should also establish role-based security and privacy training for four categories:
- Users with physical access to secure locations: Users who can enter these locations, regardless of their role in the organization
- General users: Users who are authorized to use an information system
- Privileged users: Users who have elevated access to perform sensitive functions that are restricted to general users
- Organizational personnel with security responsibilities: Stakeholders responsible for ensuring security and technology implementation must meet CJIS requirements
Document all of your training activities and maintain them for at least three years as demonstrable proof during audits.
4. Audit and Accountability
This control requires all CJI access to be monitored and logged. The best practice is to align your logging policies with your broader risk management strategy so that your audit systems capture all relevant CJI access events, such as:
- What type of access occurred
- When it happened
- Where the CJI was accessed
- Who accessed it
- What happened during the event, such as queries, edits, and exports
You must retain the above logs for at least one year or until they’re no longer needed for administrative, legal, audit, or other purposes. The goal is to have a comprehensive audit trail for accountability and traceability. Assign team members to review audit records periodically and flag risks or suspicious behavior.
5. Assessment, Authorization, and Monitoring
Maintaining CJIS controls is an ongoing effort and requires frequent assessments and monitoring for compliance. That’s why you must assign a senior official, such as a chief security officer, State Identification Bureau (SIB) chief, or an information assurance official, to oversee evaluations.
Conduct internal assessments at least annually, as well as after any significant changes, such as an update to CJIS requirements or a security incident. Document your findings and report them to the contracting agency or individual responsible for oversight. These reports must include a plan of action and milestones (PoA&M) that outlines your remediation actions.
6. Configuration Management
Under this control, all systems used to store and transmit CJI must have proper safeguards in place. To meet this requirement, document a baseline configuration and map how your network connects to CJI systems and services.
Review and update the configurations at least annually, after significant system updates, or following security incidents. Maintain at least one previous version as backup. Assign a privacy and security officer whose duty it is to review any proposed updates and then reject or approve them based on findings.
Like with other policy areas, maintain findings and update logs for at least two years.
{{cta_withimage22="/cta-blocks"}}
7. Contingency Planning
One of the goals of CJIS is to ensure CJI is available consistently. This is why the CJIS framework mandates detailed contingency plans that address adverse events.
Contingency plans should align with incident response, business continuity, and disaster recovery efforts for a coordinated approach.
For compliance, assign clear roles and responsibilities to your stakeholders, identify critical assets, and create resilience procedures that will allow you to continue business operations after a potential incident, outage, or natural disaster.
Depending on your industry, you may also need to designate alternate storage and processing sites (physically separate from your main location) that allow critical operations to resume quickly.
8. Identification and Authentication
Because CJI is highly sensitive, organizations need to implement mechanisms and processes that verify the identities of users, programs, and devices before they’re granted access to protected data.
Each access attempt must also use the ORI and additional identifiers, such as an ID or IP address, so that you have a verifiable trail of who accessed data.
As an additional measure of security beyond credentials, consider layered authentication methods, like multi-factor authentication, or other replay-resistant authenticators, such as one-time passwords or challenge-response mechanisms.
9. Incident Response
Incident response plans must meet CJIS criteria and be implemented across all levels and departments. The requirement is to create, document, and share an incident response policy that outlines the roles, responsibilities, and procedures for handling security incidents related to CJI.
Have both your security and privacy teams collaborate during the development process to ensure that the plan is comprehensive and practical. It’s best to elaborate as much as possible on the response procedures, responsible parties, and timings.
Review and update your incident response plan regularly, particularly after a security incident, in response to audit findings, and following regulatory changes.
10. Maintenance
Ongoing CJIS Security Policy compliance requires you to regularly review, repair, or replace system components related to media and information security, including hardware, so they function as intended. All on-site and off-site maintenance workflows must be reviewed and approved by relevant stakeholders.
If you need to move equipment to a different location for maintenance, you must first remove all CJI to minimize the risk of exposure. Inspect maintenance tools for unauthorized modifications and do the same for diagnostic programs before running them to check for malicious code.
Only authorized personnel should perform maintenance on CJI-related systems.
11. Media Protection
Media protection controls govern the handling of CJI throughout its entire lifecycle. The expectation is to store all media, physical and non-physical, in secure locations or control areas. Digital content should have appropriate encryption measures.
Make sure to also secure CJI in transit—establish procedures for transporting CJI out of secure locations, assign clear accountability, and implement encryption to minimize the odds of digital data being compromised.
When no longer needed, follow strict disposal procedures, such as degaussing and deleting digital media and destroying documents by cross-shredding or incinerating them.
{{cta_withimage22="/cta-blocks"}}
12. Physical and Environmental Protection
This control group primarily focuses on securing the locations where you house CJI. To comply, implement physical security measures such as:
- Locked doors
- Surveillance
- Biometric readers
- Card readers
For CJIS Security Policy compliance, you must create and maintain a list of stakeholders who may access secured locations or issue authorizations to others. Review and update this list at least annually, and after staffing changes, to ensure that only authorized personnel retain access.
It’s also essential that you maintain physical access logs and visitor records for at least one year and review them quarterly.
13. Planning
This control area requires you to create a planning policy that defines purposes, roles, and compliance practices aligned with applicable laws and regulations.
To meet this control, document and review how effectively your systems handle security and privacy throughout their lifecycle, and if they meet regulatory guidelines. Start by creating written security and privacy plans that cover each system that handles CJI. They must then be evaluated and approved by an authorizing official before use.
These plans must be thorough and contain information like:
- System roles, components, and dependencies
- Types of data processed
- Threats to the system and mitigation plans
- Personnel responsible for system security
- Implementation of security controls
Have a designated personnel to review and update your plans regularly and after any significant system changes to keep them effective.
14. Personnel Security
Insider threats pose a significant risk to security, making it essential to vet all stakeholders with potential CJI access. The requirement under CJIS is to review and update personnel security policies and procedures annually, or after audits, incidents, or regulatory changes.
Assign risk ratings to all team positions based on the level of access. Screening each stakeholder should include role-specific criteria, residency checks, and fingerprint-based investigations. If you find a stakeholder has a criminal history (like a felony or misdemeanor), delay approval until additional checks are done.
The CJIS also describes strict offboarding procedures with steps including terminating access within 24 hours, revoking authenticators and credentials, and retrieving all system security assets.
15. Risk Assessment
You’re expected to conduct regular CJI risk assessments at the organizational, process, and system levels. You need to create a policy to address areas like the purpose, scope, and management commitment regarding risk assessments within the organization. Depending on the complexity of your operations, the policy can be general or mission- and system-specific.
From a practical perspective, your risk assessments should include all potential threat vectors towards CJI systems, including third-party risk. Once you’ve completed the assessment, categorize your risks based on their likelihood and impact so that you can effectively allocate resources for remediation. Document the findings in a report, which you must review quarterly and after significant system changes.
16. Systems and Services Acquisition
Ensure that all acquired systems and services meet strict security and privacy requirements at all stages of their lifecycle: acquisition, deployment, operation, maintenance, and decommissioning.
You must document your system’s role, data type, and threat landscape, then assign individuals responsible for its security and privacy during the lifecycle. If you’re working with third parties, your contracts must explicitly include provisions that address:
- Security and privacy requirements
- Documentation and assurance expectations
- Acceptance criteria for deployment
- Details on stakeholders responsible for implementation and oversight
17. Systems and Communications Protection
This is one of the more extensive CJIS control areas. It emphasizes securing CJI during storage and transmission. It requires implementing stringent security measures that ensure the security, integrity, and confidentiality of CJI across the relevant networks and systems.
Some of the security mechanisms you need to implement include:
- DDoS protections
- Firewalls
- Limiting external access points
- Deny-by-default policies
- Encryption
18. System and Information Integrity
This control category requires regular system reviews to address flaws in your software controls and mitigate any emerging vulnerabilities. According to the framework, you can rely on automation solutions to streamline this step.
The CJIS Security Policy specifies timeframes for software updates depending on the severity of vulnerabilities identified. Apply patches by:
- 15 days for critical priority
- 30 days for high priority
- 60 days for medium priority
- 90 days for low priority
When you update your systems, test them in isolated environments to verify effectiveness and address any bugs before deployment.
19. Supply Chain Risk Management
Organizations must develop and maintain formal policies and procedures that govern how they secure third-party systems and services. The objective is to outline key responsibilities, identify supply chain risks, and guide mitigation. Review and update your policies at least annually or after a security incident.
When onboarding new vendors, make sure that their security meets CJIS criteria. Conduct detailed due diligence assessments through questionnaires. You should also build a risk management team with stakeholders from multiple departments to account for legal, security, and operational perspectives.
20. Mobile Devices
All mobile devices that may access the wireless network, such as tablets and smartphones, must be protected with policy-driven protocols, such as:
- Validation testing to ensure all access points are accounted for
- Securing access points to prevent unauthorized access and manipulation
- Enabling user authentication and encryption on management interfaces
- Disabling nonessential management protocols for access points
- Reviewing access logs at least monthly
As part of mobile device security, organizations must also implement management measures that centralize oversight of configuration controls, application usage, and actions such as locking or wiping devices remotely.
Challenges of CJIS compliance—with best practices
Due to the comprehensive nature of CJIS compliance, pursuing it can be challenging. Some of the biggest roadblocks include:
Achieve CJIS Security Policy compliance faster with Vanta
Vanta is a trust management platform that helps organizations achieve compliance with frameworks like CJIS through dedicated control resources, documentation support, and guidance. We offer out-of-the-box support for standards like ISO 27001, SOC 2, and NIST 800-53, which can help you map to CJIS requirements quickly. We can also help you build custom frameworks that cater to your unique security and compliance space.
Vanta’s compliance automation product comes with features such as:
- Continuous monitoring in a unified dashboard
- Automated evidence collection powered by 375+ integrations
- Pre-built policy and documentation templates with a built-in editor
- Automation for many repetitive compliance workflows
If your organization has already achieved compliance or is pursuing related frameworks such as NIST 800-171, FedRAMP, or CMMC, you can use Vanta’s cross-mapping to reuse existing controls and eliminate duplicative efforts.
Schedule a custom demo and see how Vanta can streamline your compliance program.
{{cta_simple41="/cta-blocks"}}





FEATURED VANTA RESOURCE
The ultimate guide to scaling your compliance program
Learn how to scale, manage, and optimize alongside your business goals.














.png)


.png)


.png)
.png)




.png)


.png)
.svg)
.svg)


