Share this article

State of third-party risk management: Expert insights and the path forward
Accelerating security solutions for small businesses Tagore offers strategic services to small businesses. | A partnership that can scale Tagore prioritized finding a managed compliance partner with an established product, dedicated support team, and rapid release rate. | Standing out from competitors Tagore's partnership with Vanta enhances its strategic focus and deepens client value, creating differentiation in a competitive market. |
In today’s fast-moving digital economy, growth depends on strong, trusted relationships with vendors, suppliers, and partners. These third parties are often essential to modern business operations; however, they also open the door to a range of risks, from regulatory fines to operational slowdowns. Many organizations have already felt the impact of these risks becoming reality firsthand.
Our State of Trust Report, which surveyed over 2,500 IT and business leaders in the U.S., U.K., and Australia, found that nearly half (46%) of all respondents experienced a data breach from a vendor after beginning their partnership.
This data makes it clear that vendor risk doesn’t end at onboarding and reinforces the need for continuous oversight through a strong third-party risk management (TPRM) program. A TPRM program will operationalize your approach to identifying, assessing, and managing the risks associated with all external vendors, suppliers, and partners that have access to your organization’s operations.
While often used interchangeably, vendor risk management (VRM) focuses specifically on a subset of third-party risks. A truly effective TPRM strategy extends beyond vendor contracts to manage risks across the full spectrum of third-party relationships—including suppliers, partners, and service providers. This means addressing multiple risk types, from cybersecurity and privacy to ESG, legal, and any reputational risks.
In this guide, we review the common challenges of TPRM strategies, explore how teams are working to close those gaps, and highlight why AI and automation are crucial for scaling TPRM efforts.
Why TPRM matters: Navigating a complex landscape
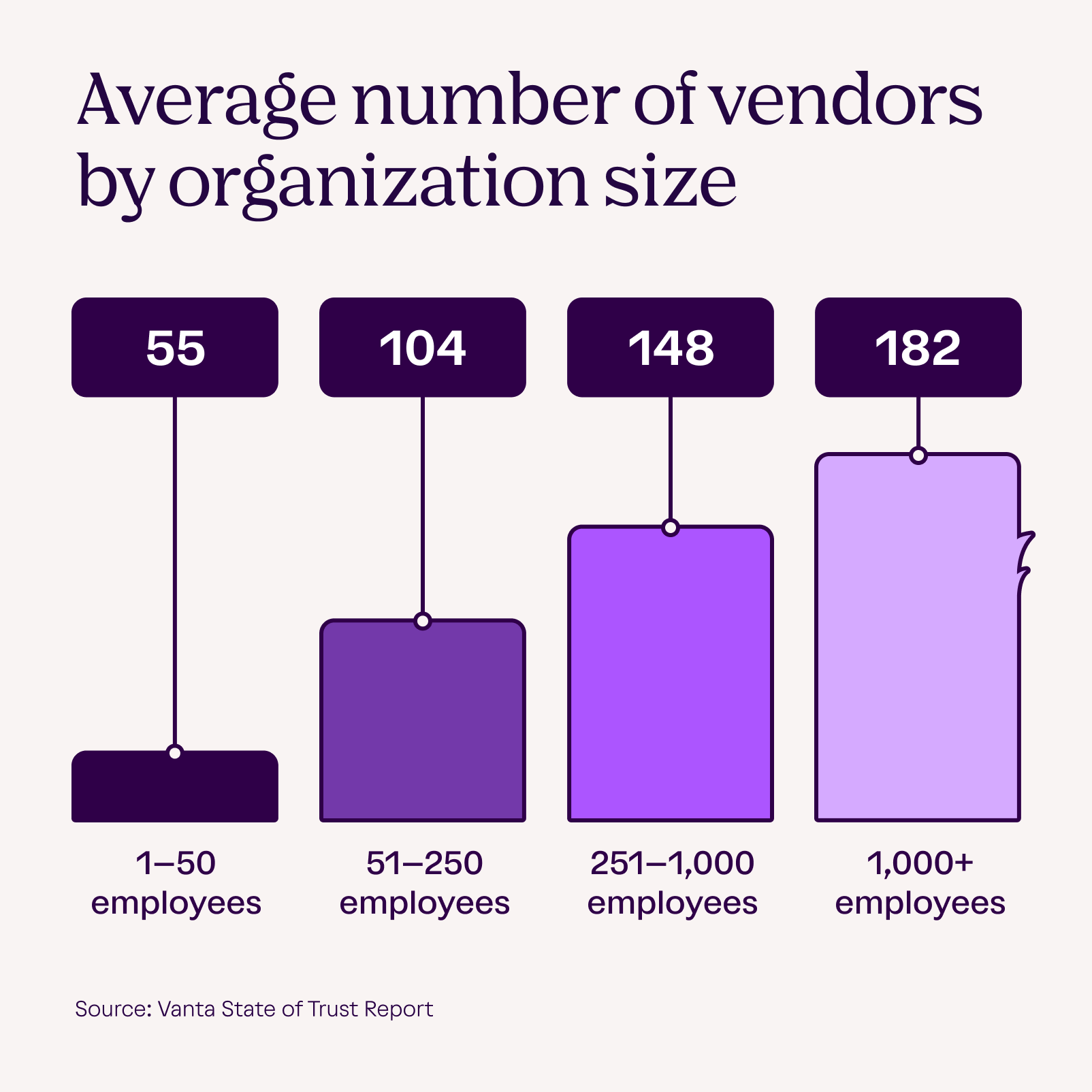
As businesses grow, so do their vendor ecosystems—and the risks that come with them. Our State of Trust Report found that organizations with 1 to 50 employees work with an average of 55 vendors. For companies with 1,000 or more employees, that number more than triples to 182.
Managing this scaling vendor footprint effectively requires a clear, structured approach to TPRM. The NIST Cybersecurity Framework (CSF) outlines four implementation tiers that help organizations identify the strength of their risk management practices:
Managing this scaling vendor footprint effectively requires a clear, structured approach to TPRM. The NIST Cybersecurity Framework (CSF) outlines four implementation tiers that help organizations identify the strength of their risk management practices:
Our Trust Maturity Report found that 77% of organizations at the “risk-informed” tier conduct formal vendor risk assessments. By the “repeatable” tier, that number climbs to nearly 100%. This trend could signal that vendor risk management is often one of the first structured practices that companies adopt as they begin to scale their TPRM efforts.
That said, as organizations scale, they may overlook less obvious risks, like unmanaged fourth-party connections, unsanctioned software use by employees (shadow IT), or inherited vulnerabilities buried deep in the supply chain.
These blind spots can undermine even well-intentioned programs, especially when security processes aren’t fully developed or consistently applied. Evan Rowse, Governance, Risk, and Compliance SME at Vanta, sees this gap all too often:
Rowse elaborates on this disconnect, pointing out that while a given individual in an organization may have a good perception of risk, the supporting organizational structures to manage what's “known” often fall short.
“Many humans are inherently good at managing risk in their own sphere of knowledge and experience,” he explains. “We all know how to cross a road safely while watching for cars, loose pebbles, and perhaps even knowing it may be icy.”
“Organization executives are usually experienced in risk assessment. However, one executive's appetite for risk is usually different from the next, and this is what makes us all human. Without a defined process, risk management efforts are likely to be misaligned until something goes wrong.”
So, what does it look like when a company is properly managing third-party risk? Rowse identified these key factors:
- Third parties are tiered and measured by criticality: Companies that excel at TPRM categorize their vendors by criticality and create structured, risk-driven review schedules. This strategic approach helps prevent over-monitoring lower-risk relationships and under-monitoring more critical threats.
- Assessments happen at onboarding and beyond: Reviewing suppliers and partners up front is important, and having a consistent cadence for reassessing top-tier vendors over time is also crucial.
- Documenting risk appetite: TPRM-savvy companies clearly outline the level of risk they’re willing to accept while pursuing their objectives. This guides decision-making and helps prevent impulsive decisions, leading to a more consistent approach to risk management.
- Board-level visibility: When third-party or supply chain risk appears on the boardroom agenda, it reflects meaningful executive alignment and long-term commitment.
Taken together, these traits demonstrate a more structured, intentional approach to TPRM. Without these practices, companies may be exposed to a complex set of third-party security risks.
Examples of third-party security risks
Third-party risk can take many forms, and not all are easy to spot. Below are some examples that underscore the need for structured oversight. This is particularly true as businesses expand their third-party partnerships and integrate emerging technologies, like AI.
- Geopolitical, jurisdictional, and concentration risks: Vendors in foreign or high-risk regions can face regulatory and supply disruptions. Moreover, relying on a few critical suppliers creates single points of failure.
- Compromised SaaS provider: When a trusted software platform suffers a breach involving sensitive customer data, the impact extends directly to the business, not just the vendor.
- Inconsistent contractor security controls: When measures like multifactor authentication or endpoint protection aren’t applied consistently to contractors and freelancers, attackers can exploit these gaps to access internal systems and sensitive data.
- Fourth-party dependency outage: If a critical vendor’s own provider fails, the disruption can cascade to your organization—even if your direct vendor is still operational.
- Expired compliance certifications: If a vendor allows a key certification or report (such as ISO 27001 or SOC 2) to lapse, it might signal internal control breakdowns or a deprioritization of compliance—both of which introduce risk to your organization.
- Unvetted SaaS tools or integrations: Also known as shadow IT, this risk occurs when third-party AI-powered tools or integrations—like adding an AI assistant to Slack—are adopted without proper vetting. While they may speed up workflows, unchecked data handling can create serious security risks. With the rapid emergence of innovative AI services, many of these unapproved tools can unintentionally expose sensitive information, violate internal security policies, or introduce compliance gaps.
How businesses approach TPRM today
TPRM relies on identifying risks through vendor security reviews. These reviews often use security questionnaires to collect a snapshot of a vendor’s security posture during onboarding or contract renewal.
Comprehensive security reviews go beyond just gathering credentials and compliance reports. They involve a structured process with key steps:
- Defining the review scope and security criteria
- Standardizing due diligence and review methods
- Assessing the vendor’s security risks
- Assigning a vendor risk score
Today’s TPRM programs, largely centered on these reviews, often include extensive document collection and risk scoring based on self-reported data from questionnaires. While these workflows offer structure, they can be time-consuming and difficult to scale as organizations add dozens or even hundreds of third-party relationships. To address these challenges, many teams turn to leading vendor risk management solutions that help streamline evidence collection, standardize assessments, and support ongoing vendor monitoring at scale.
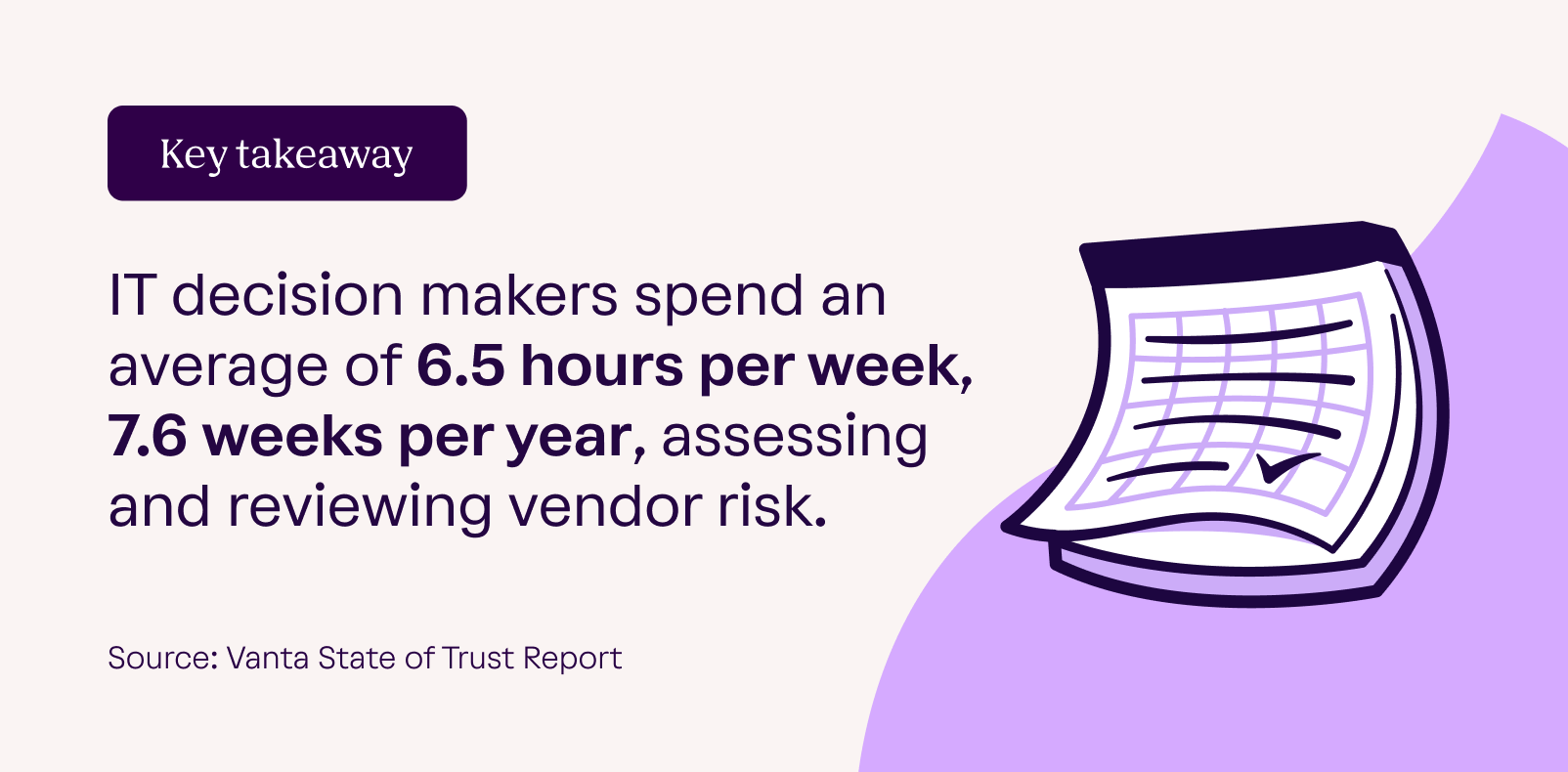
This was observed in our State of Trust Report, which reveals that IT decision-makers spend an average of 6.5 hours per week assessing and reviewing vendor risk. That adds up to 7.6 full working weeks each year.
To reduce this burden and make TPRM more scalable, Vanta’s Vendor Risk Management solution helps businesses move beyond manual workflows through:
- Automated evidence gathering
- Pre-built questionnaire templates to standardize reviews
- Automated vendor risk assessments
- Agentic AI to answer questionnaires, to extract findings from questionnaires and documents, and to answer vendor questions for faster vendor follow-up
- A unified vendor inventory and dashboard for tracking metrics
- Auto-scoring of vendor risks based on default or customizable criteria
- Continuous monitoring, so you can move from point-in-time risk assessment to truly continuous, always-on monitoring
“I believe we have only scratched the surface of how vendor risk management will evolve with the use of AI,” says Rowse. “We can already use AI to ask or respond to questions, and even conduct assessments without directly contacting a vendor. We can also monitor and analyze vendors based on publicly available information. As we can shift much of the painstaking and manual effort in conducting assessments, we can have more time to focus on what's important, like making better decisions about the relationships we hold.”
The future of TPRM
Advances in tech and growing supply chain interdependencies are reshaping how businesses identify and manage vendor risks. Here are four key trends that we predict will define the future of TPRM.
AI automation goes full circle
AI in TPRM is moving beyond current applications toward comprehensive automation of the entire risk assessment lifecycle.
"AI co-pilots will be involved in reviewing, writing, sending, and even answering questionnaires on the vendor side," explains Rowse. "AI co-pilots on the purchaser side will then assess those responses to determine what constitutes risk. I see a future of AI interacting with AI until an important decision needs human involvement."
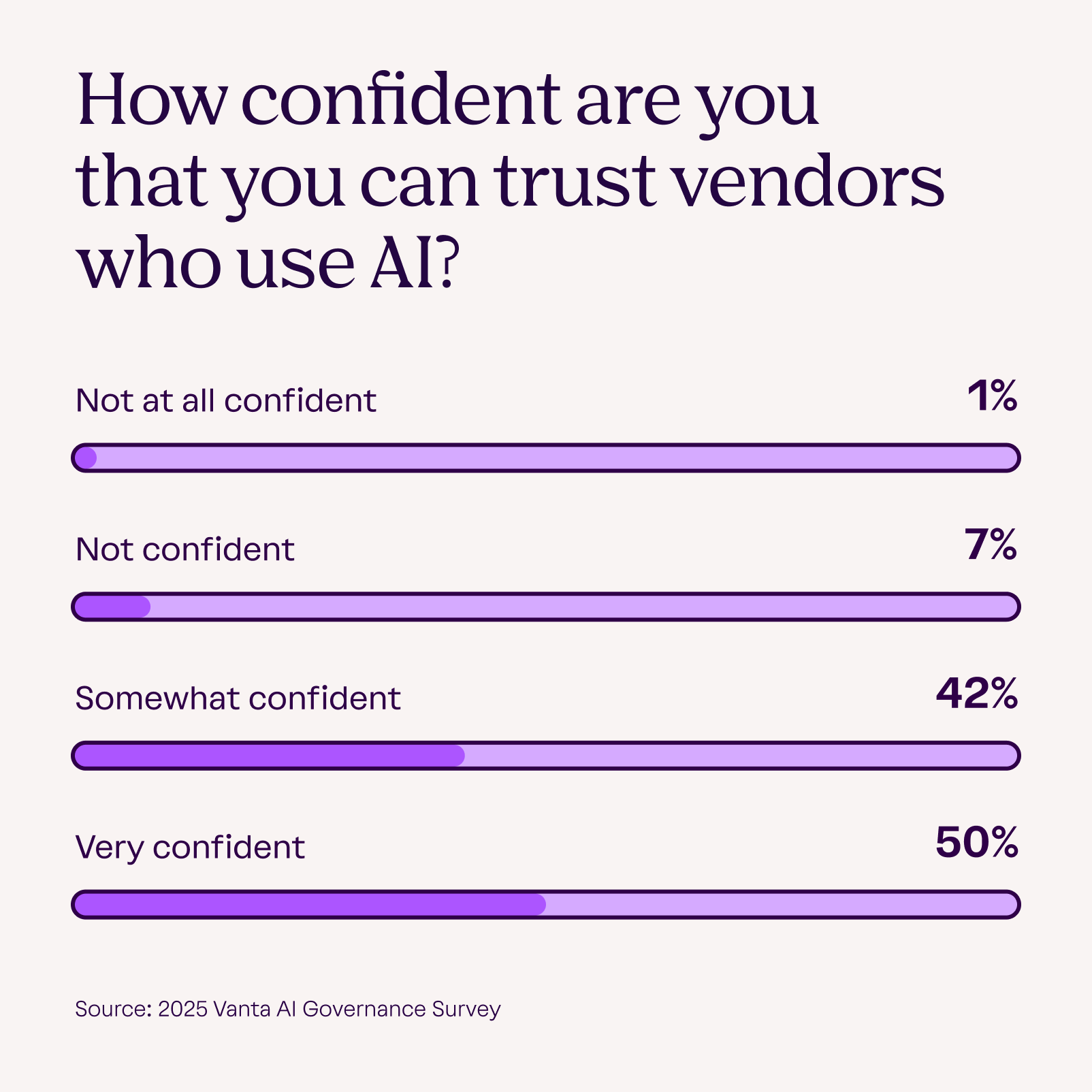
While AI introduces new risk dimensions, it's becoming increasingly important to assess how vendors use AI within their own operations. TPRM programs must now account for this, incorporating questions about AI governance, transparency, and compliance into their risk assessments. Our AI Governance Survey found that 50% of respondents were very confident in vendors using AI responsibly, while another 42% were somewhat confident—highlighting the need for TPRM practices that validate and continuously monitor vendors’ AI usage.
Always-on vendor risk monitoring becomes the norm
Vendor monitoring is evolving beyond traditional questionnaires toward sophisticated, continuous monitoring solutions that help manage risks by providing real-time insights through multiple data streams.
"Active vendor monitoring solutions have been around for a while, but will significantly improve," notes Rowse. "The solutions we have will become more sophisticated and comprehensive for certain vendor types, offering better insights into third-party issues than traditional questionnaires were ever able to uncover."
This might include monitoring public sentiment on social media for ESG risk, analyzing news feeds, and reviewing financial statements. The challenge lies in processing the massive amount of data available, drawing out relevant risk insights from the noise, and highlighting potential choices and decisions that would require human intervention.
Supply chain discovery gets smarter
Identifying and managing single points of failure is evolving from documentation to proactive discovery of critical dependencies.
Automated supply chain discovery would provide unprecedented visibility into extended vendor networks, revealing hidden connections and potential cascade failure points that traditional methods might miss.
AI-driven tools will manage data inundation
Technology can improve relationship management. But it also creates a new challenge: making sense of the sheer amount of data available to us.
"In the coming years, we'll be able to manage relationships better than ever before, as important data will be at our fingertips to help make decisions," Rowse says. "However, we'll likely be inundated with data, so having tools to make sense of it all will be essential."
Relationship management success will depend on transforming raw data into actionable insights through AI-driven analysis tools that identify patterns and emerging risks while filtering out noise and presenting information in formats that support effective decision-making.
Benefits of robust TPRM (and the cost of neglecting it)
The business case for mature TPRM extends far beyond compliance checkboxes. Organizations with robust TPRM programs could gain competitive advantages, while those that neglect it may face mounting costs or operational challenges.
Benefits of mature TPRM practices
Effective TPRM delivers measurable value across multiple dimensions of business operations:
- Stronger security posture through early detection of emerging threats and vulnerabilities before they escalate into incidents
- Easier compliance with frameworks like SOC 2, ISO 27001, GDPR, and HIPAA when vendor risk assessments are systematically documented and regularly updated
- Reduced audit burden through centralized documentation that provides readily available evidence and clear audit trails
- Increased operational resilience from a better understanding of third-party dependencies, supporting improved business continuity planning
- Better vendor relationships, as structured processes create shared expectations and clearer communication channels
- Cost savings from both breach prevention and operational efficiencies in vendor onboarding and management processes
Costs of neglecting TPRM
The consequences of inadequate TPRM and vendor risk management can be severe and far-reaching:
- Data breaches and ransomware attacks frequently originate through vulnerable vendors or the interfaces used to connect with them, creating incidents that organizations didn't directly cause but may remain responsible for addressing
- Regulatory fines, legal liability, and failed audits multiply quickly when vendor-related incidents occur, creating lasting business impacts
- Reputational harm from vendor-related incidents that erodes customer trust and damages competitive positioning
- Downtime and service outages from vendor failures that halt revenue-generating activities and damage customer relationships
- Higher cyber insurance costs or lost coverage eligibility as carriers recognize poorly managed vendor risk
Beyond these direct costs, inefficient TPRM processes create hidden operational drag that impacts strategic business objectives.
"This inefficiency often diverts personnel from other core tasks and increases the time it takes to onboard new third-party services, delaying the realization of their intended benefits," says Rowse. "Inefficient processes don't just affect taking on new vendors. Imagine a scenario where enabling an innovative new feature from one of your existing vendors, like Slack or AWS, takes multiple weeks simply due to an inefficient risk management process… This can have a huge impact on the business outcomes, especially where first to market is important."
Common TPRM challenges and how to overcome them
Despite its importance, implementing and maintaining an effective TPRM program comes with significant challenges. These often stem from the sheer volume and complexity of third-party relationships, coupled with evolving technological and regulatory landscapes.
The root of many TPRM challenges lies in the traditional approach to security questionnaires and other cumbersome processes. Matt Cooper, Director of GRC at Vanta, advocates for a fundamental shift in this approach: "If you give a vendor 400 questions, you won't get real engagement. Ask the 10 or 12 that truly matter, and they'll respond meaningfully."
This philosophy represents a shift from checkbox compliance to actionable risk assessment that strengthens vendor relationships while providing better security outcomes.
Streamline your TPRM strategy with Vanta
Ready to modernize your TPRM approach? Vanta automates questionnaire workflows, provides continuous vendor monitoring, and delivers the insights you need to make informed risk decisions.
Explore Vanta's risk assessment and management software to see how you can lead more resilient, efficient risk management programs.





FEATURED VANTA RESOURCE
The ultimate guide to scaling your compliance program
Learn how to scale, manage, and optimize alongside your business goals.














.png)

.png)

.png)
.png)
.png)


.svg)
.svg)


