Share this article

How Claude + MCP + Vanta could help auditors
Accelerating security solutions for small businesses Tagore offers strategic services to small businesses. | A partnership that can scale Tagore prioritized finding a managed compliance partner with an established product, dedicated support team, and rapid release rate. | Standing out from competitors Tagore's partnership with Vanta enhances its strategic focus and deepens client value, creating differentiation in a competitive market. |
At Vanta, we’re always looking to experiment, learn, and stay at the forefront of AI. Recently, we built a proof of concept to explore how auditors could interact more effectively with audits and the data within them. Our experiment used Anthropic’s Claude, the open source MCP (Model Context Protocol), and Vanta’s API to enable users to ask deeper questions of Vanta’s compliance data.
What is MCP?
Since the release of ChatGPT, engineers have been searching for ways to connect large language models (LLMs) with internal or proprietary data. MCP (Model Context Protocol) offers a standardized approach to this problem by defining an open protocol for LLMs to interact with local or remote data sources.
At a high-level, MCP follows a client-server architecture that allows MCP Hosts to connect to local and remote data sources. MCP Hosts, like Claude or Cursor, can leverage an MCP Client to connect to an MCP Server, like the Vanta MCP Server. That MCP Server enables defined capabilities inside of the MCP Host, such as querying Vanta for audits, controls, or evidence.

Finding a focus
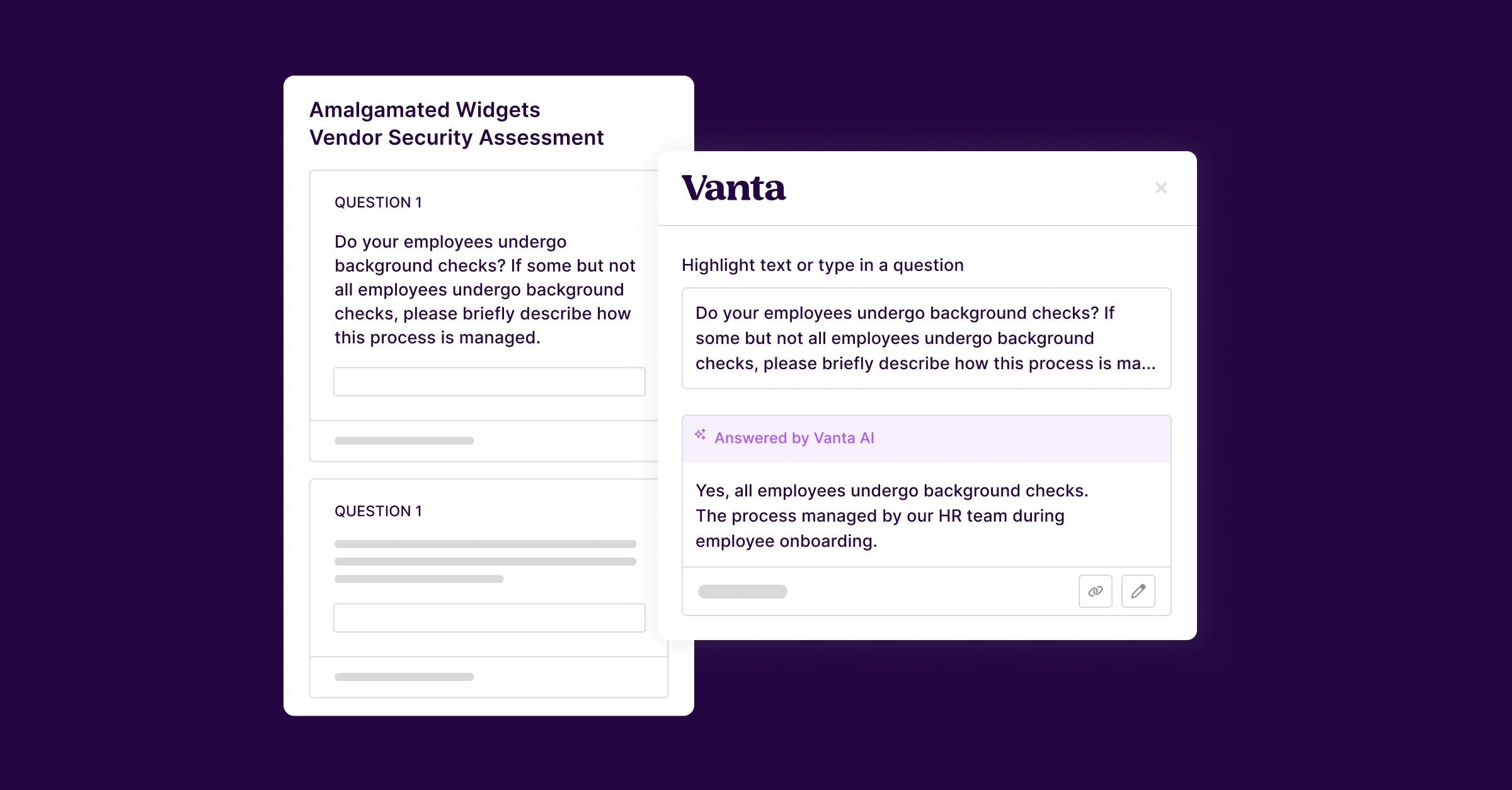
At Vanta, we’ve recently expanded our REST API, giving customers and auditors the ability to query and modify their Vanta data in whole new ways. We were able to take our REST API documentation and generate an MCP Server programmatically, allowing chatbots like Claude to understand (and use) the Vanta API. We started with a simple task: Getting Claude LLM to list my audits.
Start building

We chose Claude Desktop as our MCP Host, because of its straightforward process to integrate with MCP Servers. Claude Desktop supports modifying a configuration file to pull in MCP Servers from various sources, such as npm packages or local directories.
Here’s an example of our Claude Desktop configuration file:

Taking a deeper look, we can see that the config allows us to define a package, a command to start the server, and arguments to include. If you haven’t configured or used an MCP Server before, I found the best way to debug was to just ask Claude.

Following Claude’s instructions, we now have a running MCP Server in Claude’s Developer settings!

Back to the focus
Over a cup of coffee we have an MCP Server running, but we still have more to learn. Let’s ask Claude what we can do.

The server exposes available capabilities to Claude, and with Claude’s pre-trained context about security and compliance, we get a useful list of different capabilities built into Vanta’s API. This is done through the tools primitive and the tools/list endpoint, defined in the MCP protocol. Each tool exposes a function that can be run on the server. These functions can even be API calls. Since our server contains a “list audits” tool, we’ll try to get Claude to invoke it and get all of the audit engagements with an internal test domain, No Probllama.

Without prompting to pull the data from Vanta; Claude was able to derive my intent from the context of the question and the MCP tools it has available. It wanted to be so sure it was pulling the right No Probllama account that it included Noprobllama Support too. They have a SOC 2 Type II audit that started September 24, 2024 and ended February 1, 2025.
Let’s continue to stretch the capability and see where we can take it. Let’s make Claude find the audit we’re talking about through another description—maybe end date? Then let's find some other data about that audit, like the evidence for it, and let’s add some math for good measure.

Neat! Claude found the correct audit, looked through the evidence, and summed the count. But beyond that, it was nice enough to let me know what was ready for audit, along with some other high-level information.
Ok, let’s try two more things. Let’s see what kinds of audits we’re performing and try to export some information.


Anything Claude could do before, it can do with Vanta data now, creating visualizations and files quickly.
Conclusion
The rapid advancements in AI, including LLM-based agents, are transforming how we interact with our data. By leveraging MCP, we successfully enabled Claude to query, analyze, and visualize compliance data from Vanta in real time.
This proof of concept demonstrates the potential of AI-augmented audits—reducing manual work and empowering auditors with intelligent, context-aware insights.
Are you interested in exploring what Vanta + MCP could do for your audits? Are you interested in finding novel solutions to our customers’ problems? We’re hiring! Are you interested in learning how MCP and Vanta could help make you and your audit firm more efficient? Reach out to us at partners@vanta.com!





FEATURED VANTA RESOURCE
The ultimate guide to scaling your compliance program
Learn how to scale, manage, and optimize alongside your business goals.






















.png)


.svg)
.svg)


