Share this article
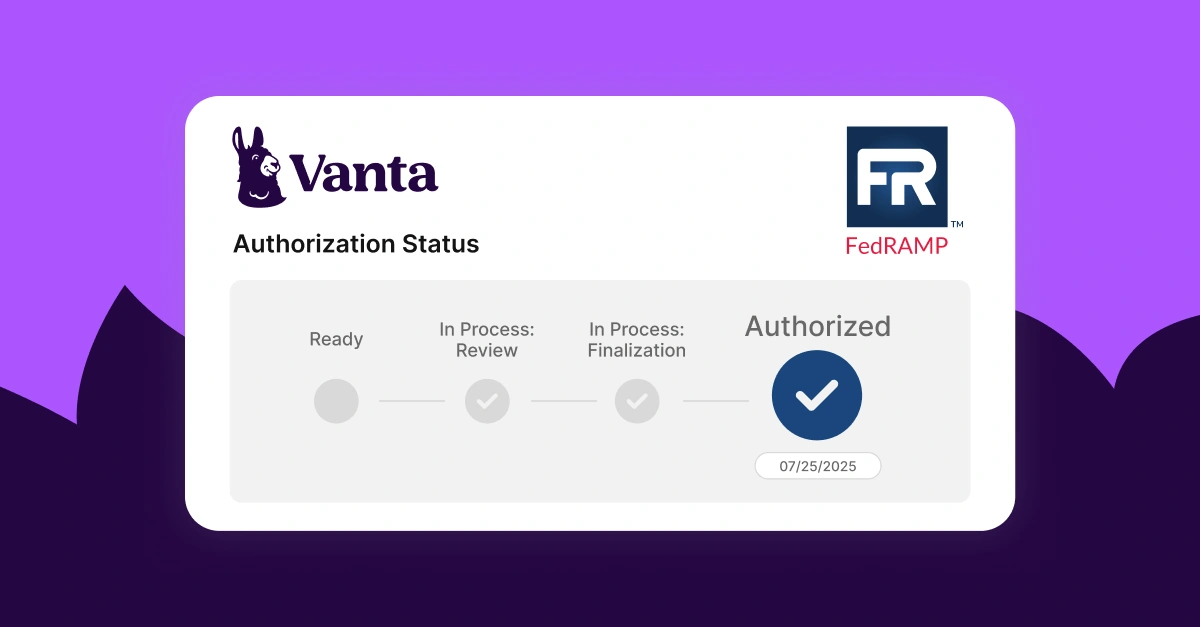
Lessons learned from Vanta’s FedRAMP® 20x pilot program
Accelerating security solutions for small businesses Tagore offers strategic services to small businesses. | A partnership that can scale Tagore prioritized finding a managed compliance partner with an established product, dedicated support team, and rapid release rate. | Standing out from competitors Tagore's partnership with Vanta enhances its strategic focus and deepens client value, creating differentiation in a competitive market. |
In late March 2025, the General Services Administration (GSA) announced the first major overhaul to FedRAMP® in over a decade, soft-launching a new, fast-track authorization path called FedRAMP 20x.
In May 2025, we submitted our initial package for the pilot, quickly followed by a resubmission of our final package. We’re now excited to share that Vanta has officially achieved FedRAMP 20x Low Authorization and a listing on the FedRAMP Marketplace. With the traditional rev 5 FedRAMP authorization path taking an average of two years or longer, this is a huge milestone for government agencies and cloud service providers alike.
The GSA and community working groups are still finetuning the FedRAMP 20x process, but our early experience with the submission process has given us a glimpse of what faster, more cost-effective, and streamlined federal compliance might look like.
Read on for three of our biggest lessons learned and what it means for teams considering this path. You can also watch our full webinar, “Inside the FedRAMP 20x Pilot: Lessons Learned with Vanta,” for a more in-depth discussion about our FedRAMP 20x submission process.
Lesson 1: FedRAMP 20x is a new process entirely
FedRAMP 20x is a new assessment model for authorization. It is designed to speed the path to FedRAMP by shifting the focus away from documentation and toward automated testing and technical validation. The 20x Phase One pilot focuses on Low authorizations, with a planned phase two for Moderate authorizations.
It’s tempting to simply think of FedRAMP 20x as a faster version of traditional FedRAMP. But in our experience, it’s a fundamentally different process. Here are a few of the major differences between traditional FedRAMP and FedRAMP 20x:
Taken together, these differences add up to a new approach to compliance that prioritizes continuous monitoring over compiling documentation for a point-in-time assessment. In other words, for a successful FedRAMP 20x submission, you’ll need to shift from a “checklist compliance” mentality to a “real-time security posture” mindset.
"At its core, I think it's a push to do better security validation. Whenever you're moving away from screenshots and point-in-time checks to something more continuous, I believe you're getting to a much stronger level of security." — Jadee Hanson, CISO at Vanta
Pro tip: Based on our experience, here are some tips on approaching this new process:
- Break it down: Use Vanta or another GRC tool to visualize the KSIs and map your evidence cleanly from the start
- Loop in your product team: Machine-readable formats aren’t a nice-to-have—they’re required. Get product involved early
- Vet your third-party auditor: Choose an auditor who can handle ambiguity and collaborate with your process—not just grade it
Lesson 2: KSIs are the future—but they require thought
One of the major differences between traditional FedRAMP and FedRAMP 20x is the use of key security indicators (KSIs). KSIs replace the traditional NIST 800-53 control mapping used in FedRAMP.
KSIs don’t require specific documentation, and there's no definitive guidebook on how to meet them. In other words, the onus is on security teams to determine what each KSI means, what they consider meaningful evidence, and what they believe are the best ways to meet the objective of each control.
This flexibility can be a double-edged sword. On one hand, KSIs shift compliance from a documentation-first approach to one rooted in real-time, operational security. Instead of proving controls through static artifacts, teams must demonstrate how those controls function in practice—creating a closer alignment between security and how systems actually run.
On the other hand, mapping evidence to KSIs requires “grey area” thinking—you must think critically about how to meet KSIs and what that evidence should look like.
"I think it's a really big step towards better security where we're not necessarily dictating every last little thing. We're allowing the cloud service provider and the security team to define some of these critical things that we would love to see in place." — Jadee Hanson, CISO at Vanta
When it comes to interpreting KSIs, here’s our advice:
- Build the right team: Bring in folks who know your control frameworks inside and out—and who aren’t afraid to work in the gray areas. Interpreting KSIs takes comfort with ambiguity and a strong sense of what “maturity” actually looks like.
- Zoom out on intent: Some KSIs (like “Rapidly mitigate vulnerabilities”) can feel hard to prove. When in doubt, step back and focus on the spirit of the requirement. What’s the goal behind the KSI—and what signals show you're hitting it?
- Group by control families: Many KSIs roll up to broader control domains. Organizing them this way makes it easier to spot overlap and decide what evidence pulls double duty.
Lesson 3: Federal compliance is inching closer to how cloud providers operate today
For years, the door to FedRAMP compliance has been closed to a wide swath of companies due to its cost, complexity, and timeline. FedRAMP 20x removes many of these barriers to entry, aligning closer to how many tech companies operate today. As a result, we expect many cloud-native, automation-first teams to enter the federal market faster. Plus, companies that receive a FedRAMP 20x Low Pilot Authorization will be prioritized for the FedRAMP 20x Moderate Pilot.
The benefits of a modernized FedRAMP go both ways, too. A streamlined compliance process opens the doors for government agencies across the board to benefit from partnerships with cloud service providers touting the latest tech and applications.
“When I think about the overall ability for government agencies and national labs and all these incredible government entities to use software, they are going to very much benefit from these great cloud service providers that have new approaches and modern tech to address threats." — Jadee Hanson, CISO at Vanta
Join the FedRAMP 20x pilot with Vanta
Vanta is one of four cloud service providers in the first cohort to successfully complete the FedRAMP 20x Phase One Pilot program. We chose to pursue this authorization as part of our broader commitment to bring trust management to government agencies and vendors.
Interested in testing the FedRAMP 20x process for your org? We’ve built out the KSI framework in our platform. Existing Vanta customers can access the pilot framework today—sign up here.





FEATURED VANTA RESOURCE
The ultimate guide to scaling your compliance program
Learn how to scale, manage, and optimize alongside your business goals.














.png)














.svg)
.svg)


