Share this article

CVE-2025-55182: The critical React RCE and the hidden risk in your supply chain
Accelerating security solutions for small businesses Tagore offers strategic services to small businesses. | A partnership that can scale Tagore prioritized finding a managed compliance partner with an established product, dedicated support team, and rapid release rate. | Standing out from competitors Tagore's partnership with Vanta enhances its strategic focus and deepens client value, creating differentiation in a competitive market. |
TL;DR
- The threat: CVE-2025-55182 is a critical Remote Code Execution vulnerability in React Server Components with a CVSS score of 10.0
- Who is affected: The vulnerability originates in React 19 and flows downstream to frameworks like Next.js (versions 15 and 16) which are vulnerable by default
- Immediate action: Patch your internal applications by updating react, react-dom, and next packages to the latest fixed versions immediately
- Supply chain risk: Since your SaaS vendors likely use these frameworks, Vanta customers should use the TPRM engine to identify vulnerable vendors and keep track of their mitigation
The critical React vulnerability explained
On December 3rd, the React team disclosed a critical security flaw in React Server Components known as CVE-2025-55182. With a CVSS score of 10.0, this issue is extremely severe. React and Next.js are the backbone of the modern web. Consequently, this vulnerability likely sits deep within your third-party vendor ecosystem in addition to your own codebase.
At Vanta, we know that securing your own perimeter is only half the battle. We have outlined what you need to know about the vulnerability, why default configurations are at risk, and how to assess your exposure across your supply chain using Vanta.
What is CVE-2025-55182?
CVE-2025-55182 is a Remote Code Execution (RCE) vulnerability that allows an attacker to take control of a server without logging in.
The flaw exists in the Flight protocol. This is the mechanism React uses to communicate between the server and the client. React fails to safely deserialize payloads sent to React Server Function endpoints. As a result, an unauthenticated attacker can craft a malicious HTTP request that executes arbitrary code when processed by the server.
Default configurations are vulnerable
The most alarming aspect of this CVE is the low barrier to entry for attackers.
Many high severity vulnerabilities require a specific feature to be enabled to create risk. That is not the case here. The official advisory explicitly states that even if your app does not implement any React Server Function endpoints, it may still be vulnerable if your app supports React Server Components.
If an application is built on a framework that supports React Server Components like Next.js App Router, the vulnerable endpoint exists by default. There is no misconfiguration required on the developer's part because simply using the framework as intended exposes the application.
Which products are affected?
The vulnerability impacts React versions 19.0.0 through 19.2.0. However, most organizations and the vendors you rely on do not install these packages directly. They consume them via frameworks. The most notable affected frameworks include:
- Next.js: Versions 15.x and 16.x are heavily impacted. Note that Next.js 14 Canary releases are also affected
- Waku: A minimal React framework
- RedwoodJS: Projects using the Redwood SDK
- React Router: Projects utilizing the new RSC capabilities
How to mitigate
If you are managing your own code, immediate action is required. The React team and Vercel have released patches.
- If you use Next.js: Upgrade immediately to the latest patch for your version, such as 15.0.5, 15.1.9, or 16.0.7. If you are on a Next.js 14 Canary release, you must downgrade to the stable v14 release.
- If you use other frameworks: Update React, React DOM, and the relevant server DOM packages to the latest versions.
- WAF rules: While some hosting providers have deployed Web Application Firewall rules to block malicious payloads, these are temporary measures. Patching is the only permanent fix.
The hidden risk: Your third-party vendors
Patching your own code is straightforward. The harder question is whether your vendors have patched theirs.
Modern SaaS is built on the same frameworks you use. If your HR portal, your analytics tool, or your marketing platform is built on Next.js 15, they are the ones holding the risk. If they are compromised, your data is compromised.
This is where third party risk management (TPRM) becomes critical. You cannot patch a vendor's code, but you can identify which vendors are high risk and demand assurance.
How Vanta helps you cut through the noise
Security teams are often flooded with generic alerts. When a critical vulnerability like CVE-2025-55182 breaks, you do not want to start checking every vendor manually. You want a platform that can tell you directly which vendor is vulnerable and cut through the noise. Vanta’s platform is designed to do exactly that so you can focus on the vendors that actually matter.
Here is how you can use the platform to pinpoint this specific risk:
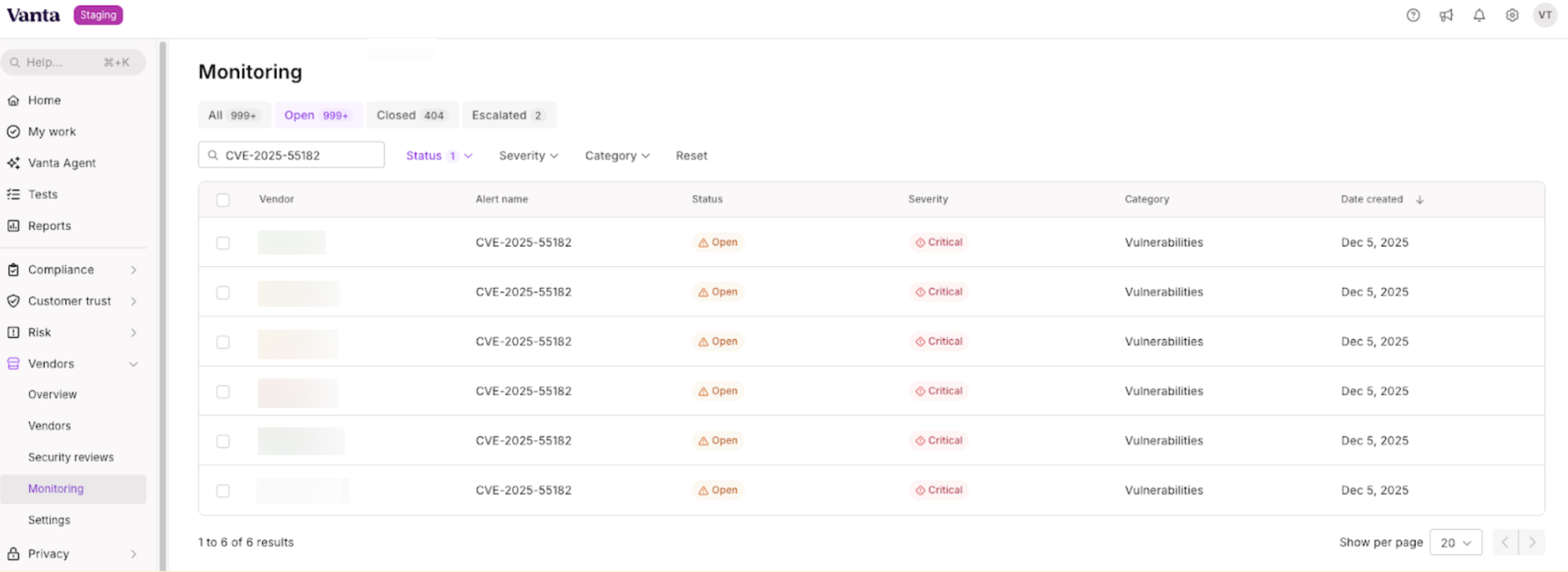
- Filter by vulnerability: You can use the Vanta platform to filter your alerts and vendor inventory specifically for CVE-2025-55182. This instantly isolates the relevant signal from the noise so you see exactly where to put your attention without wading through unrelated warnings.
- Track remediation progress: You can monitor the specific status of your vendors to see how many have resolved the issue at any given time. This visibility allows you to track the remediation rate across your supply chain and ensure your partners are actually fixing the vulnerability rather than just acknowledging it.
Next steps for Vanta customers
We’re here to help you manage this risk. If you are using Vanta for TPRM, we recommend that you visit the Monitoring tab to see all vendors affected by this vulnerability. You should reach out to these vendors if they are not remediating the vulnerability within their stated SLAs for a critical vulnerability. If a critical vendor cannot patch quickly, you must be prepared to limit their access to your data or internal networks, or temporarily pause data syncing until they are secure.





FEATURED VANTA RESOURCE
The ultimate guide to scaling your compliance program
Learn how to scale, manage, and optimize alongside your business goals.
























.png)

.svg)
.svg)
.png)
.png)
.png)