

If your organization is expanding into the healthcare sector or plans to, you will need to become compliant with the Health Insurance Portability and Accountability Act (HIPAA). Understanding protected health information (PHI) is an important first step toward achieving this goal.
Protecting sensitive patient information has been the primary goal of HIPAA since it became law in 1996. To safeguard this data effectively, HIPAA has been expanded with the Security Rule and Privacy Rule, two standards that outline strict guidelines for storing, disclosing, and disposing of PHI.
In this article, we’ll discuss:
- What qualifies as PHI under HIPAA and what doesn’t
- How to use and disclose PHI under HIPAA
- Penalties for improper PHI disclosure
How does HIPAA define PHI?
According to HIPAA, PHI is any individually identifiable health information related to a patient’s condition, treatment, or payment for care. To be considered PHI, this information must be created, received, maintained, or transmitted by a covered entity or business associate.
Covered entities are healthcare providers, health plans, and healthcare clearinghouses that transmit PHI in connection with HIPAA-regulated transactions. To help manage the volume and complexity of their patient data, covered entities often enter a business associate agreement (BAA) with third-party vendors. These are called business associates (BA) under HIPAA and include individuals and organizations that handle PHI on behalf of covered entities, such as cloud service providers or financial services.
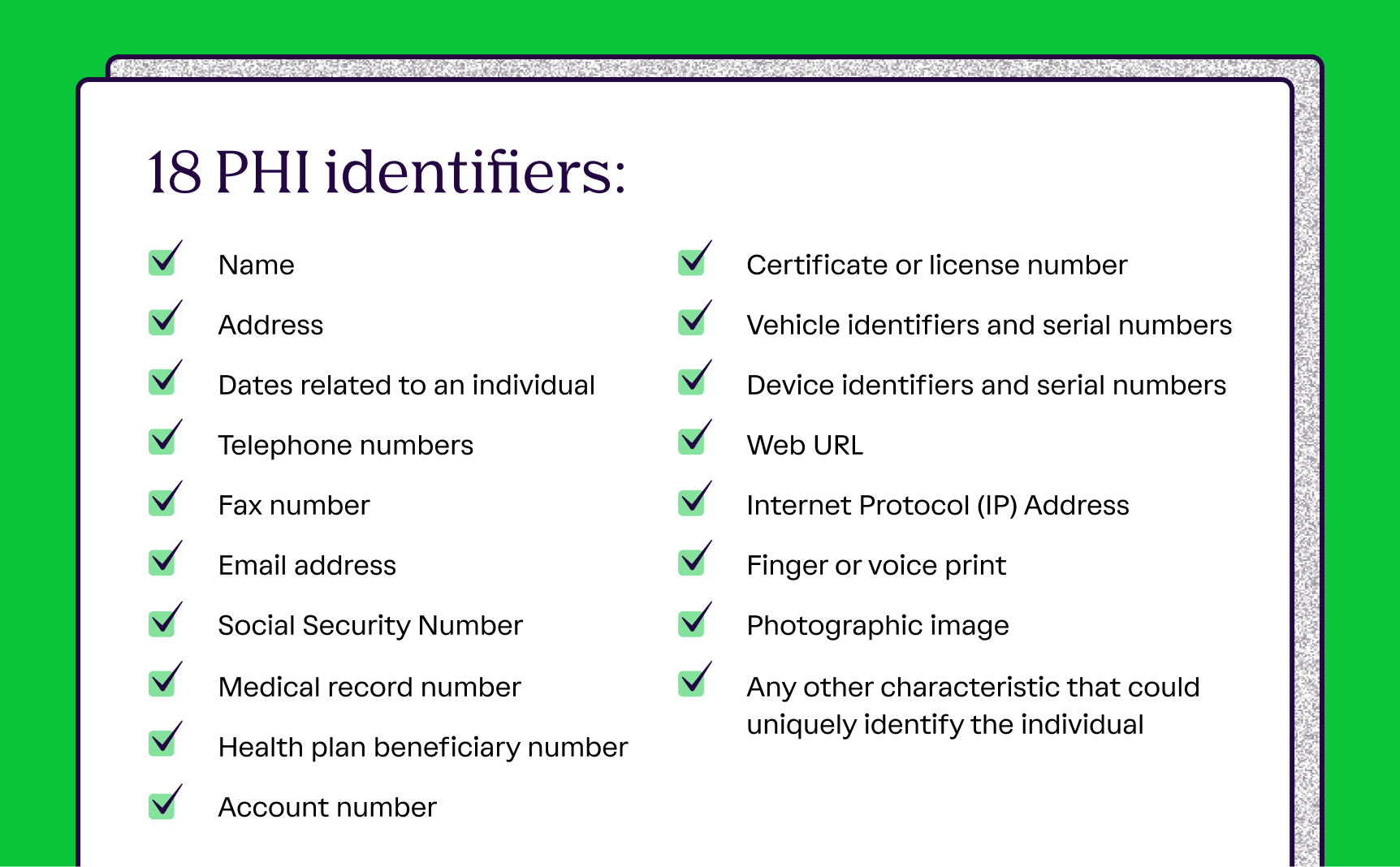
To help determine what qualifies as PHI, HIPAA specifies 18 identifiers—pieces of data associated with individually identifiable health information that include information such as:
- Patient’s legal name
- Biometric identifiers
- Social Security number
- Email address
- Phone number
However, this doesn’t mean that all health information is automatically considered PHI. For instance, the statement “Mr. Smith has a broken arm” is only considered PHI if it is created, stored, or transmitted by a covered entity or business associate.
What isn’t considered PHI?
HIPAA also provides clear guidelines for when health information doesn’t fall under its scope, even if it meets PHI criteria. A common example is patient information maintained in medical facilities of educational institutions, such as schools and universities. Examples include the nurse’s office, on-campus health centers, and behavioral or psychological counseling services offered by educational institutions.
Even though the records maintained in such facilities may contain individually identifiable health information, they directly relate to a student, meaning they’re considered educational records governed by the Family Educational Rights and Privacy Act (FERPA), not HIPAA. FERPA-covered information like immunization or therapy notes are therefore considered part of a student’s educational records.
Another exemption from HIPAA is health records maintained by employers. Although they may contain employee health information, such as absences due to illness, they’re considered part of employment records, not PHI.
You can also ensure that data is no longer considered PHI by removing all 18 HIPAA identifiers, so that it can no longer be linked to specific individuals. However, this method isn’t infallible. Large datasets or those that record rare cases carry the risk of re-identification, particularly when cross-referenced with external information.
{{cta_withimage13="/cta-blocks"}} | HIPAA compliance checklist
Can non-health information be considered PHI?
Yes, non-health information is considered PHI under HIPAA once it becomes linked to a health record stored, used, or accessed by a covered entity or business associate, even though it isn’t medical in nature.
You’ll note that the 18 identifiers of PHI under HIPAA include non-health information such as an insurance ID number, ZIP code, or email address. What matters is context—to illustrate, an individual’s name and phone numbers aren’t considered PHI by default. However, if a covered entity or business associate includes them in a designated record set that contains individually identifiable health information, they will be considered PHI under HIPAA.
Similarly, information about a person’s job title isn’t PHI by default, but when combined with the diagnosis of a rare genetic disorder, it can be considered as such.
Ideally, organizations should evaluate non-health information on a case-by-case basis to see if HIPAA obligations are triggered. It’s also important to have vetted de-identification protocols if such data has to be used for training or research.
What happens if PHI is disclosed in violation of HIPAA?
When an organization violates HIPAA provisions by disclosing PHI without authorization, the U.S. Department of Health and Human Services (HHS) Office for Civil Rights (OCR), HIPAA’s primary enforcer, may take a range of actions depending on the severity of the violation. In most cases, the enforcement is non-punitive and may include:
- Voluntary compliance
- Technical guidance
- A resolution agreement
However, if the violation is severe or not addressed in a satisfactory or timely manner, the OCR may escalate enforcement actions to include:
- Civil penalties
- Criminal charges
1. Civil penalties
Depending on the severity and the nature of the violation, it may be placed into one of four tiers, which affects the amount of the fine.
The table below outlines the criteria for each tier, as well as the corresponding financial penalties as of August 8, 2024:
Note: While the table above reflects official penalty amounts, the OCR issued a Notice of Enforcement Discretion in 2019 stating the annual penalty limits in three of the penalty tiers would be reduced according to the HITECH Act’s language. As such, the maximum and annual penalty limits could be considerably lower, especially taking into account annual inflation increases.
HIPAA also sets an annual limit on penalties per provision. This cap applies to multiple violations of the same requirement, but can exceed it when different provisions are breached.
2. Criminal charges
If a covered entity or business associate knowingly violates HIPAA, it may face criminal charges. The Department of Justice handles these violations instead of the OCR.
Criminal charges are classified into three tiers, with escalating criteria and terms:
In cases where the violating entity financially benefits from the breach, they may also receive a monetary fine, along with having to refund any profits.
How you can ensure PHI is secured
Protecting PHI isn’t a one-time effort—you need to establish proactive measures that address the full lifecycle of your data, from creation and storage to use and disposal. Without ongoing measures, security practices may fall short over time.
Here are three key steps you can take to ensure PHI remains secure:
- Conduct regular training
- Establish access control
- Maintain detailed documentation
Step 1: Conduct regular training
Comprehensive staff training and education are essential to creating a first line of defense for PHI. You should hold regular training sessions to ensure your team members understand what constitutes PHI, how they should handle it, and what creates privacy risks.
As part of your training, include clear procedures for responding to requests for patient information, using the appropriate channels, and disposing of PHI appropriately. Ongoing awareness campaigns and training are the most efficient ways to minimize the risk of unauthorized disclosures and create a culture of compliance.
Step 2: Establish access control
As part of HIPAA compliance, you’ll have to implement the Minimum Necessary Rule, which requires limiting access, use, and disclosure of PHI to the minimum amount necessary for individuals to perform their roles effectively.
Another effective measure to implement is role-based access controls that align PHI permissions with specific roles or responsibilities. By ensuring that only the appropriate team members have access to sensitive data, you reduce the risk of improper disclosures, unauthorized access, and insider threats.
Remember that PHI must also be physically safeguarded. As per Vanta’s HIPAA Violation Survey, lost or stolen devices that store PHI are among the top five causes of reported violations. So, implement strict safeguards to restrict access to such assets.
{{cta_withimage39="/cta-blocks"}} | The Healthcare compliance checklist
Step 3: Maintain detailed documentation
As part of continuous compliance efforts, you’ll need to create and collect thorough documentation of all access logs, training records, and breach reports, which helps secure PHI.
With visibility into every access event, you can quickly identify if a breach occurs and address the risk. This will minimize the potential operational and reputational damage and provide demonstrable evidence of efforts in good faith to the OCR when necessary.
Collecting this documentation manually often requires your security and compliance teams to sift through systems across disparate departments, diverting time and resources away from more strategic tasks. You can reduce the fatigue and related risks for your team by leveraging automation software to streamline these workflows and protect PHI more efficiently.
Build secure PHI practices with Vanta
Vanta is an end-to-end trust management platform that helps organizations achieve HIPAA compliance and maintain PHI integrity by offering structured resources across controls, policies, and documentation. It minimizes ambiguity during HIPAA compliance, streamlining efforts and saving time and resources for your team.
The platform offers a dedicated HIPAA product equipped with multiple features to automate tedious compliance workflows, including:
- Ready-to-use document templates
- Policy templates and a built-in editor
- A unified dashboard to streamline tracking
- Automated evidence collection through 375+ integrations
- Built-in guidance and training solutions
If your organization is pursuing other frameworks within the healthcare ecosystem, like HITRUST, NIST, SOC 2, or ISO 27001, you can leverage Vanta’s cross-mapping feature to reuse existing controls.
Book your personalized Vanta demo to see how the HIPAA suite can optimize your security and compliance efforts.
{{cta_simple18="/cta-blocks"}} | HIPAA product page
A note from Vanta: Vanta is not a law firm, and this article does not constitute or contain legal advice or create an attorney-client relationship. When determining your obligations and compliance with respect to relevant laws and regulations, you should consult a licensed attorney.

Introduction to HIPAA
What is considered PHI under HIPAA?

Looking to streamline the work for HIPAA compliance?
If your organization is expanding into the healthcare sector or plans to, you will need to become compliant with the Health Insurance Portability and Accountability Act (HIPAA). Understanding protected health information (PHI) is an important first step toward achieving this goal.
Protecting sensitive patient information has been the primary goal of HIPAA since it became law in 1996. To safeguard this data effectively, HIPAA has been expanded with the Security Rule and Privacy Rule, two standards that outline strict guidelines for storing, disclosing, and disposing of PHI.
In this article, we’ll discuss:
- What qualifies as PHI under HIPAA and what doesn’t
- How to use and disclose PHI under HIPAA
- Penalties for improper PHI disclosure
How does HIPAA define PHI?
According to HIPAA, PHI is any individually identifiable health information related to a patient’s condition, treatment, or payment for care. To be considered PHI, this information must be created, received, maintained, or transmitted by a covered entity or business associate.
Covered entities are healthcare providers, health plans, and healthcare clearinghouses that transmit PHI in connection with HIPAA-regulated transactions. To help manage the volume and complexity of their patient data, covered entities often enter a business associate agreement (BAA) with third-party vendors. These are called business associates (BA) under HIPAA and include individuals and organizations that handle PHI on behalf of covered entities, such as cloud service providers or financial services.
To help determine what qualifies as PHI, HIPAA specifies 18 identifiers—pieces of data associated with individually identifiable health information that include information such as:
- Patient’s legal name
- Biometric identifiers
- Social Security number
- Email address
- Phone number
However, this doesn’t mean that all health information is automatically considered PHI. For instance, the statement “Mr. Smith has a broken arm” is only considered PHI if it is created, stored, or transmitted by a covered entity or business associate.

What isn’t considered PHI?
HIPAA also provides clear guidelines for when health information doesn’t fall under its scope, even if it meets PHI criteria. A common example is patient information maintained in medical facilities of educational institutions, such as schools and universities. Examples include the nurse’s office, on-campus health centers, and behavioral or psychological counseling services offered by educational institutions.
Even though the records maintained in such facilities may contain individually identifiable health information, they directly relate to a student, meaning they’re considered educational records governed by the Family Educational Rights and Privacy Act (FERPA), not HIPAA. FERPA-covered information like immunization or therapy notes are therefore considered part of a student’s educational records.
Another exemption from HIPAA is health records maintained by employers. Although they may contain employee health information, such as absences due to illness, they’re considered part of employment records, not PHI.
You can also ensure that data is no longer considered PHI by removing all 18 HIPAA identifiers, so that it can no longer be linked to specific individuals. However, this method isn’t infallible. Large datasets or those that record rare cases carry the risk of re-identification, particularly when cross-referenced with external information.
{{cta_withimage13="/cta-blocks"}} | HIPAA compliance checklist
Can non-health information be considered PHI?
Yes, non-health information is considered PHI under HIPAA once it becomes linked to a health record stored, used, or accessed by a covered entity or business associate, even though it isn’t medical in nature.
You’ll note that the 18 identifiers of PHI under HIPAA include non-health information such as an insurance ID number, ZIP code, or email address. What matters is context—to illustrate, an individual’s name and phone numbers aren’t considered PHI by default. However, if a covered entity or business associate includes them in a designated record set that contains individually identifiable health information, they will be considered PHI under HIPAA.
Similarly, information about a person’s job title isn’t PHI by default, but when combined with the diagnosis of a rare genetic disorder, it can be considered as such.
Ideally, organizations should evaluate non-health information on a case-by-case basis to see if HIPAA obligations are triggered. It’s also important to have vetted de-identification protocols if such data has to be used for training or research.
What happens if PHI is disclosed in violation of HIPAA?
When an organization violates HIPAA provisions by disclosing PHI without authorization, the U.S. Department of Health and Human Services (HHS) Office for Civil Rights (OCR), HIPAA’s primary enforcer, may take a range of actions depending on the severity of the violation. In most cases, the enforcement is non-punitive and may include:
- Voluntary compliance
- Technical guidance
- A resolution agreement
However, if the violation is severe or not addressed in a satisfactory or timely manner, the OCR may escalate enforcement actions to include:
- Civil penalties
- Criminal charges
1. Civil penalties
Depending on the severity and the nature of the violation, it may be placed into one of four tiers, which affects the amount of the fine.
The table below outlines the criteria for each tier, as well as the corresponding financial penalties as of August 8, 2024:
Note: While the table above reflects official penalty amounts, the OCR issued a Notice of Enforcement Discretion in 2019 stating the annual penalty limits in three of the penalty tiers would be reduced according to the HITECH Act’s language. As such, the maximum and annual penalty limits could be considerably lower, especially taking into account annual inflation increases.
HIPAA also sets an annual limit on penalties per provision. This cap applies to multiple violations of the same requirement, but can exceed it when different provisions are breached.
2. Criminal charges
If a covered entity or business associate knowingly violates HIPAA, it may face criminal charges. The Department of Justice handles these violations instead of the OCR.
Criminal charges are classified into three tiers, with escalating criteria and terms:
In cases where the violating entity financially benefits from the breach, they may also receive a monetary fine, along with having to refund any profits.
How you can ensure PHI is secured
Protecting PHI isn’t a one-time effort—you need to establish proactive measures that address the full lifecycle of your data, from creation and storage to use and disposal. Without ongoing measures, security practices may fall short over time.
Here are three key steps you can take to ensure PHI remains secure:
- Conduct regular training
- Establish access control
- Maintain detailed documentation
Step 1: Conduct regular training
Comprehensive staff training and education are essential to creating a first line of defense for PHI. You should hold regular training sessions to ensure your team members understand what constitutes PHI, how they should handle it, and what creates privacy risks.
As part of your training, include clear procedures for responding to requests for patient information, using the appropriate channels, and disposing of PHI appropriately. Ongoing awareness campaigns and training are the most efficient ways to minimize the risk of unauthorized disclosures and create a culture of compliance.
Step 2: Establish access control
As part of HIPAA compliance, you’ll have to implement the Minimum Necessary Rule, which requires limiting access, use, and disclosure of PHI to the minimum amount necessary for individuals to perform their roles effectively.
Another effective measure to implement is role-based access controls that align PHI permissions with specific roles or responsibilities. By ensuring that only the appropriate team members have access to sensitive data, you reduce the risk of improper disclosures, unauthorized access, and insider threats.
Remember that PHI must also be physically safeguarded. As per Vanta’s HIPAA Violation Survey, lost or stolen devices that store PHI are among the top five causes of reported violations. So, implement strict safeguards to restrict access to such assets.
{{cta_withimage39="/cta-blocks"}} | The Healthcare compliance checklist
Step 3: Maintain detailed documentation
As part of continuous compliance efforts, you’ll need to create and collect thorough documentation of all access logs, training records, and breach reports, which helps secure PHI.
With visibility into every access event, you can quickly identify if a breach occurs and address the risk. This will minimize the potential operational and reputational damage and provide demonstrable evidence of efforts in good faith to the OCR when necessary.
Collecting this documentation manually often requires your security and compliance teams to sift through systems across disparate departments, diverting time and resources away from more strategic tasks. You can reduce the fatigue and related risks for your team by leveraging automation software to streamline these workflows and protect PHI more efficiently.
Build secure PHI practices with Vanta
Vanta is an end-to-end trust management platform that helps organizations achieve HIPAA compliance and maintain PHI integrity by offering structured resources across controls, policies, and documentation. It minimizes ambiguity during HIPAA compliance, streamlining efforts and saving time and resources for your team.
The platform offers a dedicated HIPAA product equipped with multiple features to automate tedious compliance workflows, including:
- Ready-to-use document templates
- Policy templates and a built-in editor
- A unified dashboard to streamline tracking
- Automated evidence collection through 375+ integrations
- Built-in guidance and training solutions
If your organization is pursuing other frameworks within the healthcare ecosystem, like HITRUST, NIST, SOC 2, or ISO 27001, you can leverage Vanta’s cross-mapping feature to reuse existing controls.
Book your personalized Vanta demo to see how the HIPAA suite can optimize your security and compliance efforts.
{{cta_simple18="/cta-blocks"}} | HIPAA product page
A note from Vanta: Vanta is not a law firm, and this article does not constitute or contain legal advice or create an attorney-client relationship. When determining your obligations and compliance with respect to relevant laws and regulations, you should consult a licensed attorney.

Explore more HIPAA articles
Introduction to HIPAA
HIPAA requirements
Preparing for HIPAA compliance
Streamlining HIPAA compliance
Get started with HIPAA:
Start your HIPAA journey with these related resources.

An 8-step HIPAA compliance checklist to meet privacy and security requirements
Use this handy HIPAA compliance checklist to ensure adherence to the key requirements.

HIPAA violations in 2025: Staff mistakes and vendor blind spots
Discover what a HIPAA violation is, common causes behind violations

Live Demo: Automating Compliance for SOC 2, ISO 27001, HIPAA, and More
Discover how Vanta’s automation and AI tools can help your team simplify compliance, strengthen security, and scale trust across frameworks like SOC 2, ISO 27001, HIPAA, and more.




