

There are many factors in your SOC 2 compliance journey that can influence the time it takes for you to get your final SOC 2 report. How long it takes for you to get your SOC 2 will depend on how many of the SOC 2 controls you need to implement, the type of audit you choose, and how well you’ve prepared for your audit.
In this article, we’ll go over the factors that will impact your SOC 2 audit timeline, break down the time frame for each of the steps, and give some tips for accelerating your SOC 2 timeline.
SOC 2 audit timelines
There are two types of SOC 2 reports: SOC 2 Type 1 or SOC 2 Type 2.
A SOC 2 Type 1 report evaluates the design of your controls (which are used to meet the SOC 2 criteria) at a single point in time. It answers the question: “Are the controls suitably designed to meet the trust service criteria as of a particular date?” This audit date is agreed upon between you and the auditor. A Type 1 report typically takes less time than a Type 2 report.
Vanta tip: The auditor may request and review evidence prior to the audit date to test a control.
A SOC 2 Type 2 report evaluates both the design and operating effectiveness of your controls over a period of time. It answers the question: “Were these controls suitably designed and operated effectively throughout the review period?” The audit window for a SOC 2 Type 2 is between three months to a year, depending on the length you choose.
During or after your audit window (depending on your auditor), evidence is reviewed by the auditor firm to show proof of design (Types 1 and 2) and operating effectiveness (Type 2) of your controls. Once all evidence is reviewed, the audit firm works with you to finalize the SOC 2 report.
{{cta_withimage1="/cta-blocks"}}
SOC 2 Type 1 audit timeline
In most cases, a SOC 2 Type 1 audit will take between five weeks and two months to complete. The auditor you choose and how well you prepare for your audit will impact your SOC 2 Type 1 audit timeline. Here are some additional factors that will also impact your timeline:
- How easily your auditor can access your evidence
- The size of your organization
- The complexity of your infrastructure
- How quickly you follow up on requests and questions from your auditor
A SOC 2 Type 1 provides a point-in-time look at your controls as of a certain date. A SOC 2 Type 1 is the most cost-effective option because it is less time-intensive than a SOC 2 Type 2.
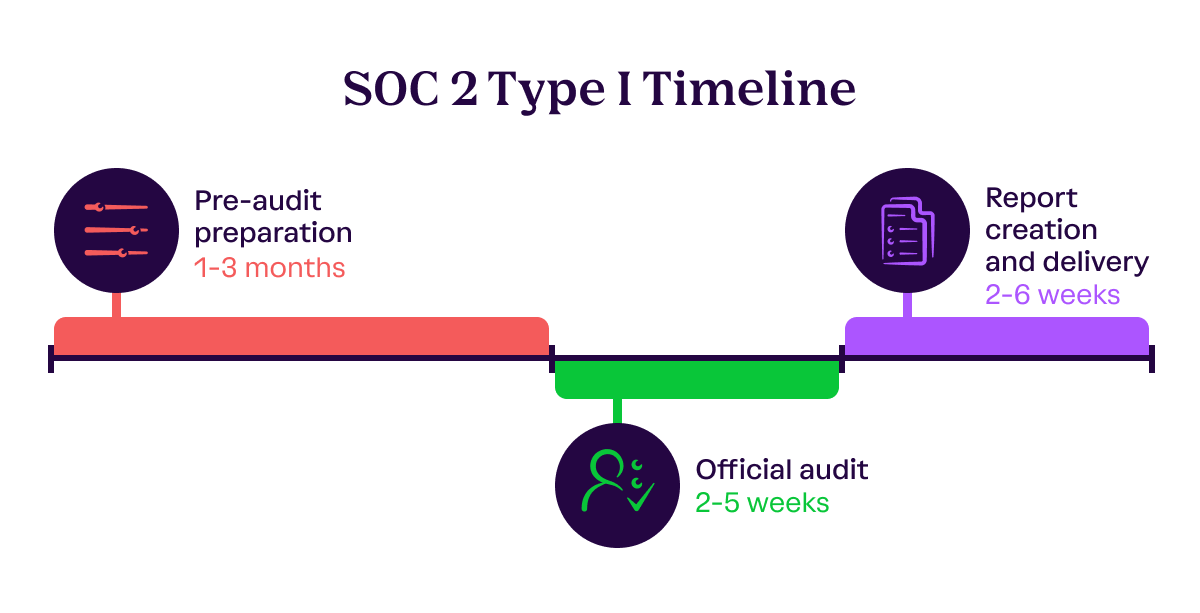
Pre-audit preparation | 1-3 months
Before your audit, you’ll need to determine which systems will be in scope for the audit, as well as which trust services criteria you want your auditor to review. Every SOC 2 report must have the security trust services criteria in scope.
You can add availability, confidentiality, processing integrity, and privacy as well. Adding these additional criteria is often driven by customer demand and usually incurs an additional fee.
Next, make sure you have controls in place to meet the SOC 2 criteria. Think of a control as a safeguard or check that enforces how your organization protects systems and data, and mitigates security risks. These often include controls around access management and data encryption, creating business-wide security policies, monitoring for software vulnerabilities, screening vendors, and conducting risk assessments.
Once you’ve prepared your controls, hire an accredited auditor. Ask your auditor what tests, documents, and policies they will need to start the audit.
The time this phase takes will depend on how many of the relevant SOC 2 controls you already have in place and how many you still need to implement.
Official audit | 2-5 weeks
After you’ve hired an auditor, reviewed your in-scope systems and controls, agreed upon timelines, and made sure that all evidence is ready, your auditor will start their audit review.
The auditor will spend time reviewing evidence, asking follow-up questions, and investigating controls to see if they were suitably designed to meet trust service criteria. Respond promptly to your auditor’s questions and requests during this period to accelerate the audit process.
Report creation and delivery | 2-6 weeks
Once your auditor has completed their evidence review, they’ll let you know if they found any exceptions (i.e., issues) with controls they reviewed. Depending on the nature of the exception, your auditor will let you know the impact on the SOC 2 trust services criteria.
Your auditor will then work with you to create your SOC 2 report. Make sure the system description in the report is accurate and reply to all auditor comments about the report promptly.
Your auditor will first present you with a draft report to review. Next, they’ll generate your final SOC 2 Type 1 report. The report details your information security practices and controls, and includes your auditor’s determination of whether they meet SOC 2 criteria. You can present this report to prospects, customers, and partners to show what measures you have in place to protect data.
SOC 2 Type 2 audit timeline
SOC 2 Type 2 audits evaluate your compliance over a period of time. You can choose the length of this audit window, which is typically between three months to a year. The added detail provided by a SOC 2 Type 2 reassures stakeholders that you’ll protect their data.
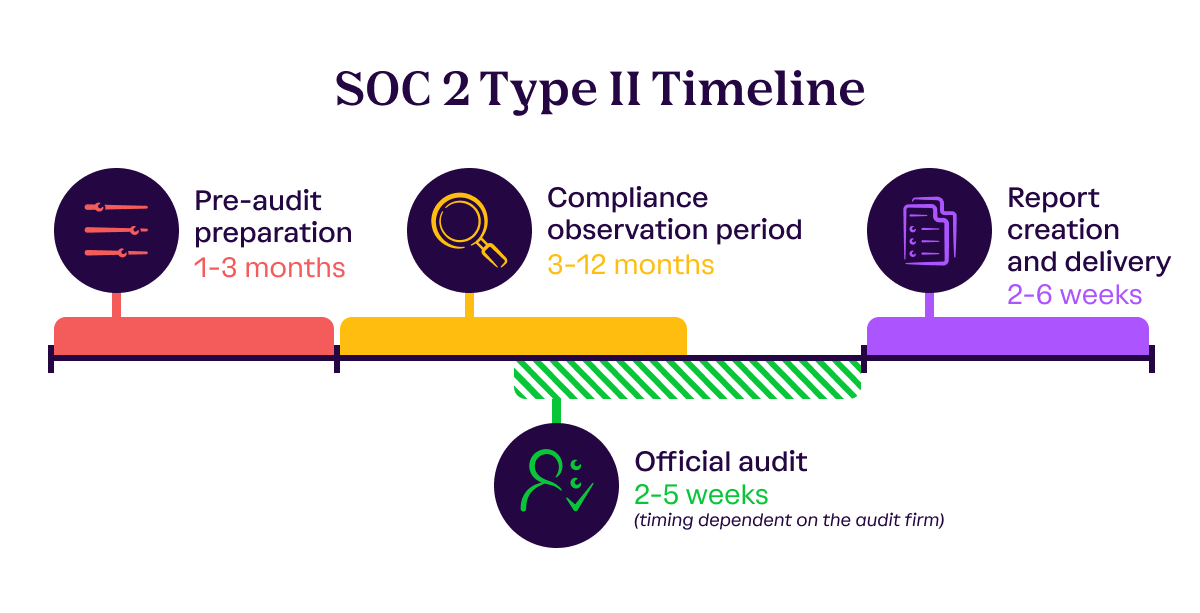
Pre-audit preparation | 1-3 months
Much like a SOC 2 Type 1, you’ll also need to implement the appropriate SOC 2 controls to address areas of non-compliance for a SOC 2 Type 2 report.
Often, a SOC 2 Type 2 report occurs after a Type 1 report. Track any areas of improvement or exceptions from your Type 1 report to resolution as you prepare for a Type 2.
The length of your preparation phase will depend on how many of the applicable controls you already have in place and how many you still need to add. Once your controls are ready, you’ll need to hire an AICPA-accredited auditor to conduct your SOC 2 Type 2 audit.
Compliance observation period | 3-12 months
The biggest difference between a SOC 2 Type 1 and SOC 2 Type 2 audit is the length of the audit window. During your observation period, your auditor will review whether controls were designed appropriately and are operating effectively.
You get to choose how long your observation period is, commonly ranging anywhere from three to six, nine, or twelve months. Early-stage organizations often opt for their first observation window to be shorter so they can get their SOC 2 report back faster. Larger and more established organizations tend to choose a one-year audit window. After companies finish their first SOC 2 Type 2, the following review periods are typically set to 12-month windows.
Official audit | 2-5 weeks
For a SOC 2 Type 2 audit, your auditor will review the documentation used to meet your controls to determine if you meet the SOC 2 criteria in scope. Depending on the audit firm, this review can occur during the observation window or shortly thereafter.
Upload evidence and complete any required activities that must be done before the end of the observation window in a timely manner. Your auditor will have months of information to review, so their audit period will take longer depending on the length of your observation window. During this period, it’s important to respond promptly to the auditor’s requests and questions to accelerate the audit process.
Report creation and delivery | 2-6 weeks
Once your auditor has completed their audit, they will compile their findings into a SOC 2 Type 2 report. Make sure the system description in the report is accurate and reply to all auditor comments about the report promptly.
The auditor will present you with a draft to review before issuing the final report. This report will detail your information security posture, the SOC 2 controls you have in place, and if they were designed appropriately and were operating effectively over the period of time to meet the SOC 2 criteria in scope. You can show this report to prospects, customers, or other stakeholders when they ask for your SOC 2 Type 2.
How long does it take to get a SOC 2 report?
From scoping your report to implementing the controls to undergoing a SOC 2 audit, the entire SOC 2 compliance process can vary greatly. Your SOC 2 timeline will vary based on the structure and size of your organization, the type of data you process or manage for your customers, the type of SOC 2 report you pursue, and whether you use compliance automation to streamline the process. We highly recommend speaking to your auditor about timelines, the estimated report issuance date, and expectations for response times.
Speed up your SOC 2 timeline with automated compliance
Getting a SOC 2 tends to be a long and complicated process, but it doesn’t have to be. With compliance automation, you can get your SOC 2 faster. Vanta’s trust management platform with compliance automation capabilities can help you streamline your SOC 2 and get your completed report in half the time.
Here’s what an automated SOC 2 process can look like with Vanta:
- Connect your infrastructure to the Vanta platform with our 200+ built-in integrations.
- Assess your risk holistically from one unified view.
- Identify areas of non-compliance with in-platform notifications.
- Get a checklist of actions to help you make the needed changes.
- Automate evidence collection and centralize all your documents in one place.
- Find a Vanta-vetted auditor within the platform.
- Streamline reviews by giving your auditor the information in your Trust Center.
- Complete your SOC 2 in half the time.
By using Vanta, you can save your business valuable time and money during your SOC 2 audit process. Learn how you can get your SOC 2 faster by requesting a demo.
A note for Vanta customers: These timelines are rough estimates. You should speak with your auditor to confirm all timelines before making commitments to external parties about report issuance dates. Delays in timelines and report issuance will occur if you do not:
- Respond to audit firm follow-ups on time
- Make payments on time
- Have a majority of Vanta tests ready by the time of review by the audit firm
- Complete all evidence submissions within agreed-upon timelines
- Utilize the Vanta tool
- Integrate all of the in-scope systems for the audit with Vanta
{{cta_simple1="/cta-blocks"}}

Preparing for a SOC 2 audit
How long does a SOC 2 audit take?

Preparing for a SOC 2 audit
How long does a SOC 2 audit take?

Download the checklist
Looking to automate up to 90% of the work for SOC 2 compliance?
There are many factors in your SOC 2 compliance journey that can influence the time it takes for you to get your final SOC 2 report. How long it takes for you to get your SOC 2 will depend on how many of the SOC 2 controls you need to implement, the type of audit you choose, and how well you’ve prepared for your audit.
In this article, we’ll go over the factors that will impact your SOC 2 audit timeline, break down the time frame for each of the steps, and give some tips for accelerating your SOC 2 timeline.
SOC 2 audit timelines
There are two types of SOC 2 reports: SOC 2 Type 1 or SOC 2 Type 2.
A SOC 2 Type 1 report evaluates the design of your controls (which are used to meet the SOC 2 criteria) at a single point in time. It answers the question: “Are the controls suitably designed to meet the trust service criteria as of a particular date?” This audit date is agreed upon between you and the auditor. A Type 1 report typically takes less time than a Type 2 report.
Vanta tip: The auditor may request and review evidence prior to the audit date to test a control.
A SOC 2 Type 2 report evaluates both the design and operating effectiveness of your controls over a period of time. It answers the question: “Were these controls suitably designed and operated effectively throughout the review period?” The audit window for a SOC 2 Type 2 is between three months to a year, depending on the length you choose.
During or after your audit window (depending on your auditor), evidence is reviewed by the auditor firm to show proof of design (Types 1 and 2) and operating effectiveness (Type 2) of your controls. Once all evidence is reviewed, the audit firm works with you to finalize the SOC 2 report.
{{cta_withimage1="/cta-blocks"}}
SOC 2 Type 1 audit timeline
In most cases, a SOC 2 Type 1 audit will take between five weeks and two months to complete. The auditor you choose and how well you prepare for your audit will impact your SOC 2 Type 1 audit timeline. Here are some additional factors that will also impact your timeline:
- How easily your auditor can access your evidence
- The size of your organization
- The complexity of your infrastructure
- How quickly you follow up on requests and questions from your auditor
A SOC 2 Type 1 provides a point-in-time look at your controls as of a certain date. A SOC 2 Type 1 is the most cost-effective option because it is less time-intensive than a SOC 2 Type 2.

Pre-audit preparation | 1-3 months
Before your audit, you’ll need to determine which systems will be in scope for the audit, as well as which trust services criteria you want your auditor to review. Every SOC 2 report must have the security trust services criteria in scope.
You can add availability, confidentiality, processing integrity, and privacy as well. Adding these additional criteria is often driven by customer demand and usually incurs an additional fee.
Next, make sure you have controls in place to meet the SOC 2 criteria. Think of a control as a safeguard or check that enforces how your organization protects systems and data, and mitigates security risks. These often include controls around access management and data encryption, creating business-wide security policies, monitoring for software vulnerabilities, screening vendors, and conducting risk assessments.
Once you’ve prepared your controls, hire an accredited auditor. Ask your auditor what tests, documents, and policies they will need to start the audit.
The time this phase takes will depend on how many of the relevant SOC 2 controls you already have in place and how many you still need to implement.
Official audit | 2-5 weeks
After you’ve hired an auditor, reviewed your in-scope systems and controls, agreed upon timelines, and made sure that all evidence is ready, your auditor will start their audit review.
The auditor will spend time reviewing evidence, asking follow-up questions, and investigating controls to see if they were suitably designed to meet trust service criteria. Respond promptly to your auditor’s questions and requests during this period to accelerate the audit process.
Report creation and delivery | 2-6 weeks
Once your auditor has completed their evidence review, they’ll let you know if they found any exceptions (i.e., issues) with controls they reviewed. Depending on the nature of the exception, your auditor will let you know the impact on the SOC 2 trust services criteria.
Your auditor will then work with you to create your SOC 2 report. Make sure the system description in the report is accurate and reply to all auditor comments about the report promptly.
Your auditor will first present you with a draft report to review. Next, they’ll generate your final SOC 2 Type 1 report. The report details your information security practices and controls, and includes your auditor’s determination of whether they meet SOC 2 criteria. You can present this report to prospects, customers, and partners to show what measures you have in place to protect data.
SOC 2 Type 2 audit timeline
SOC 2 Type 2 audits evaluate your compliance over a period of time. You can choose the length of this audit window, which is typically between three months to a year. The added detail provided by a SOC 2 Type 2 reassures stakeholders that you’ll protect their data.

Pre-audit preparation | 1-3 months
Much like a SOC 2 Type 1, you’ll also need to implement the appropriate SOC 2 controls to address areas of non-compliance for a SOC 2 Type 2 report.
Often, a SOC 2 Type 2 report occurs after a Type 1 report. Track any areas of improvement or exceptions from your Type 1 report to resolution as you prepare for a Type 2.
The length of your preparation phase will depend on how many of the applicable controls you already have in place and how many you still need to add. Once your controls are ready, you’ll need to hire an AICPA-accredited auditor to conduct your SOC 2 Type 2 audit.
Compliance observation period | 3-12 months
The biggest difference between a SOC 2 Type 1 and SOC 2 Type 2 audit is the length of the audit window. During your observation period, your auditor will review whether controls were designed appropriately and are operating effectively.
You get to choose how long your observation period is, commonly ranging anywhere from three to six, nine, or twelve months. Early-stage organizations often opt for their first observation window to be shorter so they can get their SOC 2 report back faster. Larger and more established organizations tend to choose a one-year audit window. After companies finish their first SOC 2 Type 2, the following review periods are typically set to 12-month windows.
Official audit | 2-5 weeks
For a SOC 2 Type 2 audit, your auditor will review the documentation used to meet your controls to determine if you meet the SOC 2 criteria in scope. Depending on the audit firm, this review can occur during the observation window or shortly thereafter.
Upload evidence and complete any required activities that must be done before the end of the observation window in a timely manner. Your auditor will have months of information to review, so their audit period will take longer depending on the length of your observation window. During this period, it’s important to respond promptly to the auditor’s requests and questions to accelerate the audit process.
Report creation and delivery | 2-6 weeks
Once your auditor has completed their audit, they will compile their findings into a SOC 2 Type 2 report. Make sure the system description in the report is accurate and reply to all auditor comments about the report promptly.
The auditor will present you with a draft to review before issuing the final report. This report will detail your information security posture, the SOC 2 controls you have in place, and if they were designed appropriately and were operating effectively over the period of time to meet the SOC 2 criteria in scope. You can show this report to prospects, customers, or other stakeholders when they ask for your SOC 2 Type 2.
How long does it take to get a SOC 2 report?
From scoping your report to implementing the controls to undergoing a SOC 2 audit, the entire SOC 2 compliance process can vary greatly. Your SOC 2 timeline will vary based on the structure and size of your organization, the type of data you process or manage for your customers, the type of SOC 2 report you pursue, and whether you use compliance automation to streamline the process. We highly recommend speaking to your auditor about timelines, the estimated report issuance date, and expectations for response times.
Speed up your SOC 2 timeline with automated compliance
Getting a SOC 2 tends to be a long and complicated process, but it doesn’t have to be. With compliance automation, you can get your SOC 2 faster. Vanta’s trust management platform with compliance automation capabilities can help you streamline your SOC 2 and get your completed report in half the time.
Here’s what an automated SOC 2 process can look like with Vanta:
- Connect your infrastructure to the Vanta platform with our 200+ built-in integrations.
- Assess your risk holistically from one unified view.
- Identify areas of non-compliance with in-platform notifications.
- Get a checklist of actions to help you make the needed changes.
- Automate evidence collection and centralize all your documents in one place.
- Find a Vanta-vetted auditor within the platform.
- Streamline reviews by giving your auditor the information in your Trust Center.
- Complete your SOC 2 in half the time.
By using Vanta, you can save your business valuable time and money during your SOC 2 audit process. Learn how you can get your SOC 2 faster by requesting a demo.
A note for Vanta customers: These timelines are rough estimates. You should speak with your auditor to confirm all timelines before making commitments to external parties about report issuance dates. Delays in timelines and report issuance will occur if you do not:
- Respond to audit firm follow-ups on time
- Make payments on time
- Have a majority of Vanta tests ready by the time of review by the audit firm
- Complete all evidence submissions within agreed-upon timelines
- Utilize the Vanta tool
- Integrate all of the in-scope systems for the audit with Vanta
{{cta_simple1="/cta-blocks"}}





Explore more SOC 2 articles
Introduction to SOC 2
Preparing for a SOC 2 audit
SOC 2 reporting and documentation
Streamlining SOC 2 compliance
SOC differences and similarities
Additional SOC 2 resources
Get started with SOC 2
Start your SOC 2 journey with these related resources.

The SOC 2 Compliance Checklist
Simplify and expedite your company’s SOC 2 audit and report process with Vanta. This checklist walks through the SOC 2 attestation process.

Vanta in Action: Compliance Automation
Demonstrating security compliance with a framework like SOC 2, ISO 27001, HIPAA, etc. is not only essential for scaling your business and raising capital, it also builds an important foundation of trust.



